1 Introduction
Fraud is a major cost to businesses worldwide. Multiple reporting sources estimate that total related cybercrime costs will reach $2 trillion globally in 2019 and will rise to $6 trillion by 2021. Banking, finance, payment services, and retail are some of the most frequent objectives of fraudsters, as expected. However, insurance, gaming, telecommunications, health care, cryptocurrency exchanges, travel and hospitality, and real estate are increasingly targeted as cybercriminals have realized that most online services trade in monetary equivalents. Moreover, after years in the sights of cybercriminals, banking and finance in general are better secured than other industries, so fraudsters attack any potentially lucrative target of opportunity. Fraud perpetrators also continually diversify their Tactics, Techniques, and Procedures (TTPs).
Online fraud comes in several major forms:
- Account Takeover (ATO) - most often occur when fraudsters use breached passwords and credential stuffing attacks to execute unauthorized transactions
- New Account Fraud (NAF) - sometimes called Synthetic Fraud, can be more difficult to detect and have advantages for attackers. This type involves gathering bits of PII (Personally Identifiable Information) on legitimate persons to construct illegitimate accounts. Educational, financial, and medical records can be sources of PII used for assembling fake accounts, which are then often used to launch attacks and/or are used as mule accounts to move money around
- Insider Fraud - includes not only financial theft by employees, contractors, or partners, but also the theft of intellectual property (IP), which may include customer information from CRM systems
- Screen Scraping – programmatically scraping information entered into web forms by consumers and sending to other web services. This technique is (unfortunately, because it is insecure) sometimes used for legitimate purposes
- Inventory Skimming or Depletion – perpetrated largely by bots that buy up a retailer’s inventory to re-sell
- Fraudulent Insurance Claim Submission – insurance agents’ and brokers’ credentials are captured and used to authorize fraudulent insurance claims
- Real Estate Escrow Mis-Direct – real estate agents’ credentials are captured and used to send emails to customers to have them transfer large sums (down payments) to fraudsters’ accounts. These transfers are usually unrecoverable and can be devastating to home buyers
- Banking Overlays – malicious apps that look like login screens for mobile banking apps, designed to harvest credentials and hijack transactions
- Travel Site Overlays - malicious apps that look like login screens for mobile travel apps, designed to harvest credentials and hijack transactions
One of the chief mitigations against these types of fraud is risk-based multi-factor authentication (MFA). Strong authentication or MFA can eliminate a substantial portion of ATOs by increasing authentication assurance levels. Risk-based MFA often includes mechanisms to increase identity assurance, such as identity proofing, user behavioral analytics, and behavioral/passive biometrics. Insider Fraud is handled differently due to the fact that in many cases, the access policy conditions are met because the individual(s) are authorized. Thus, monitoring and user behavioral analysis are key deterrents; and implementing the principles of least privilege and separation of duties are important to limit possible damage by insiders.
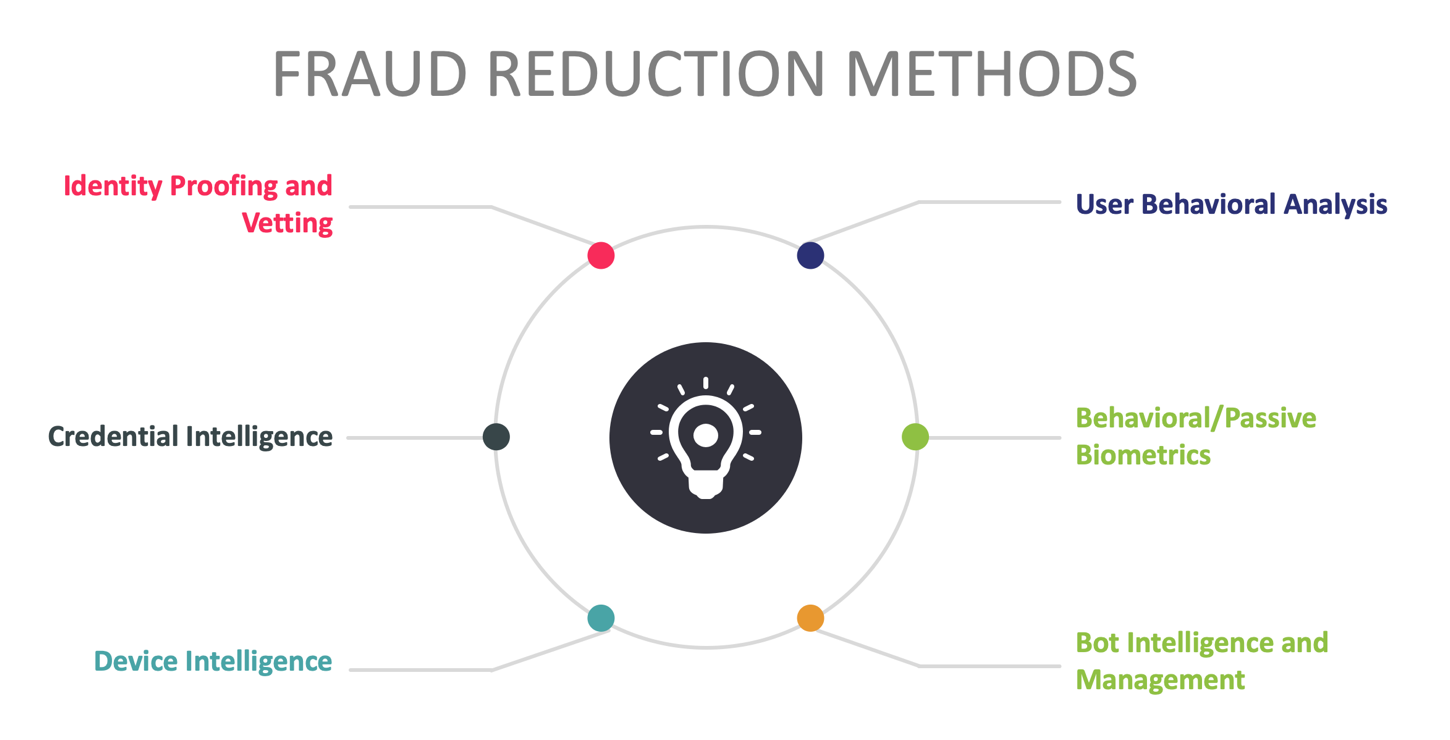
Risk-based MFA is characterized by transaction-time evaluation of multiple factors, including information about users, their devices, and the environments from which requests emanate. Risk-based MFA solutions operate optimally when integrated with or informed by Fraud Reduction Intelligence Platforms (FRIPs). FRIPs provide to risk-based MFA and transaction processing systems the information needed to make more accurate decisions on whether or not transactions should execute. FRIP solutions generally provide up to six major functions:
- Identity proofing/vetting
- Credential intelligence
- Device intelligence
- User behavioral analysis
- Behavioral/passive biometrics
- Bot detection & management
FRIP solutions also can interoperate with transaction processing systems, evaluating the context of each transaction request against pre-determined policies (similarly to authentication decisions in risk-based authentication systems) and then outputting risk scores. In these use cases, customers of FRIP solutions usually must write a bit of code to have their transaction processing systems query the FRIP service providers’ APIs. For example, a FRIP customer will collect transaction context information and transmit that as part of the API call to the FRIP service. The FRIP solution analyzes the transaction request context, gathers additional intelligence relevant to the user and request in real-time, scores it in accordance with customer-determined policies, then returns the risk score to the calling customer. The customer’s transaction processing logic than executes, taking into consideration the risk score from the FRIP service.
1.1 Market Segment
The Fraud Reduction Intelligence Platform market is mature and growing, with some vendors offering full-featured solutions providing comprehensive functionality addressing each of the major methods listed above to support millions of users and billions of transactions across every industrial sector. As will be reflected in this report, the solutions in this space are quite diverse. Some vendors have about every feature one could want in a FRIP service, while others are more specialized, and thus have different kinds of technical capabilities. For example, some vendors are highly adept at device intelligence, including detailed histories of devices and information provided by working relationships with Mobile Network Operators (MNOs), but may not offer bot detection & management. Others excel at user behavioral analysis and passive biometrics, but don’t do identity proofing. In general, identity proofing and vetting is quite specialized and is not found in all FRIP services.
Furthermore, KuppingerCole research indicates that the particular market segments that vendors choose to target often has a direct effect on the type of features available in their FRIP solutions. Some vendors specialize strictly in preventing fraud in financial transactions. Others are more general purpose, offering their services for insurance, health care, gaming, etc.











































