Playlist
Cybersecurity Leadership Summit 2019
Videos from the Cybersecurity Leadership Summit 2019 in Berlin, Germany
Show more
27 videos in this playlist
Event Recording
René Grob - Migration to a Modern IAG Solution - Experiences of Helsana Versicherungen AG
Dec 12, 2019
For over 12 years, Helsana used an IAM solution based on NetIQ Identity Manager, which was extended and adapted to individual needs. Not only did the system's maintainability suffer as a result, but its usability also no longer met today's expectations. A new, leaner and more modern system with SailPoint IdentityIQ should not only help to standardize the processes, but also offer the possibility to tackle old and new challenges in the field of IAM/IAG. It shows where Helsana was at the beginning of the project, where she is today and what the company has learned along the way.
Event Recording
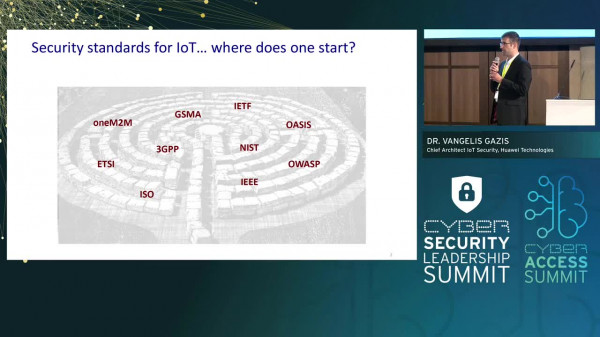
Dr. Vangelis Gazis - IoT Security: A Standards’ Perspective
Dec 12, 2019
The Internet of Things tends to mean different things to different people. This diversity of understandings makes it hard to pick up speed in joint efforts to improve the security of IoT. Fortunately, recent developments in international collaboration, particularly in standardisation initiatives, have started to bear fruits in this direction. This talk will introduce the landscape of standardisation IoT security, highlighting particular areas of technical significance to security and where improvements are challenging. In addition, areas where standardisation initiatives have been...

Event Recording
Assaf Pilo - AI as an Enabler for Detecting PI Across Large Data Infrastructures
Dec 12, 2019
Using intelligent insights on the readiness of data to move to the cloud and a dynamic catalog ready to manage it, companies can accelerate migration with both confidence and control.

Event Recording
Christoph Weiss - Next Generation ML based Data Intelligence Around Process Automation (DSGVO, GDPR, etc.)
Dec 12, 2019

Event Recording
John Tolbert - The Information Protection Lifecycle
Dec 12, 2019
Too often those of us in the cybersecurity space get wrapped up in comparing, deploying, and managing point solutions. While this is a necessary consequence of both the fragmented nature of the market and the highly specialized nature of our work, sometimes we need to step back and look at the big picture. What kind of information am I charged with protecting? How can I discover and keep track of it all? What kinds of controls can I apply? How can data be protected in different environments, on different platforms, etc? We'll look at the various stages in the life and death of information...

Event Recording
Klara Jordan - The Forgotten Story of Cyber Hygiene
Dec 12, 2019

Event Recording
Dr. Komitas Stepanyan - Auditing Cybersecurity Governance: Putting the Elephant in the Fridge
Dec 12, 2019
The term Cyber sounds very attractive and everyone wants to use this term nowadays. Although many people talk about cybersecurity, however only some of them pay some attention to cybersecurity governance. On the one hand, it is a challenge for top management to govern cybersecurity on the other hand it is challenge for internal audit to give an appropriate assurance on cybersecurity. Should Internal Audit give an assurance on cybersecurity – that is one of the most difficult questions? If yes – how? If not – who should? Cybersecurity is more about people, management...

Event Recording
Per Thorsheim - The Real Cost of Cyber Security Incidents
Dec 12, 2019
We see stories on data breaches every week, happening due to weak cyber security. Massive fines are issued based on GDPR, PCI, and consumer protection around the world. Proactive. fast & efficient handling of cyber security incidents is a key to survival for any organisation, but there are also costs that are rarely mentioned: the personal consequences for those affected by a data breach.

Event Recording
Philipp Schneidenbach - Inflections of Elections – When Ballot Rigging Meets Fraud Prevention
Dec 12, 2019
Voting is said to be the first of all citizens duties. No matter what is to be decided: Not voting is said to be a societal taboo.
Scandals around the world raise questions about the security of voting and election systems: Manipulations by election staff, inside jobs at polling locations and blatantly insecure systems. All this has been there since decades, but why does it happen again and again? What can be done to mitigate risk? And how can the current discussion about digital trust and privacy help identify solutions for the future? Acquire an in-depth overview of the key facts and...

Event Recording
Klara Jordan - Operationalizing Election Security Guidance
Dec 12, 2019

Event Recording
Panel - New Cybersecurity Challenges: Cyber-conflitcs in Perspective
Dec 12, 2019

Event Recording
Dr. Heiko Klarl - Everything as Code – Ensuring Compliance and Governance for IAM
Dec 12, 2019

Event Recording
Per Thorsheim - Password Security in 2019 - More Important Than Ever Before!
Dec 12, 2019
There is no other computer related issue that affects more people globally and more frequently than passwords. We can easily authenticate
100 times day using pins, passwords, biometrics, cards and other technologies. At the same time we see time and again that weaknesses, vulnerabilities and flaws in these mechanisms are exploited to gain unlawful access to systems and data. New consensus on passwords & digital authentication exist, but a major challenge persist: how do convince everyone we've done passwords wrong for 30 years, and need to change everything? This talk will provide...

Event Recording
Tom Janetscheck - Threat Hunting with the Microsoft Cloud
Dec 12, 2019
With the preview-release of Azure Sentinel, Microsoft has shifted some features from Azure Security Center to its new threat hunting solution. But how do all the security tools Microsoft offers nowadays integrate with each other? How can you find a way through this security jungle? And how do you make sure to have the right tools in place when it comes to protecting your IT environments and hunting threats? Join cloud security expert and Microsoft MVP Tom Janetscheck for this demo-rich session to get all these questions answered and to learn how to protect your resources easily and...

Event Recording
Jean-Christophe Gaillard - The Language of Security
Dec 12, 2019
How the way we talk about information security has changed over the last 2 decades, based on a quantitative analysis of 17 Global Information Security Surveys by EY (2002-2019)
Event Recording
Philipp Veronesi - Engineering Cybersecurity – The Knowledge Gap in Automotive
Dec 12, 2019
Cybersecurity is by far no temporary fashion. The automotive industry now realizes the importance of cybersecurity for its organization and particularly for its products. However, a large gap exists between the requirements that result from new standards and the existing knowledge within the organization. This frequently results in diffuse solutions to establish required principles of cybersecurity. In this context, many enterprises still underestimate that cybersecurity needs to be applied along the entire product lifecycle. Due to this, many companies try to close the knowledge gap via...
Event Recording
Benjamin T. Schlabs - Embracing the Human Factor
Dec 12, 2019
IT security departments are no longer just responsible for securing digital assets and appliances. They must - with equal priority - help create a secure environment that inspires productivity and empowers employees to innovate.
In this talk, we discuss challenges faced by large enterprises around embracing the Human Factor (security awareness, phishing / social engineering, password hygiene/policies, etc.). We also share insights into how key security indicators such as overall vulnerability levels and basic security hygiene can be measured and compared across organizations,...

Event Recording
Dr. Mariarosaria Taddeo - The Risk of Trusting AI in Cybersecurity
Dec 04, 2019

Event Recording
Ola Sergatchov - Beyond Cloud - the Place Where Security, DevOps and Business Meet
Dec 04, 2019
As a result of the continous evolution of IT platforms, new environments and applications show up to simplify our lives. Some receive them with suspicion, others embrace them. But security challenges don't change, they just multiply. Visibility and segmentation cannot be a roadblock on the never-ending quest for innovation and business agility.
Ola Sergatchov, Vice President of Corporate Strategy at Guardicore, in her presentation, will explore how we can deliver more with less. How to accelerate while reducing security risks, and most importantly, align...
Event Recording
Dr. Heiko Klarl - Challenges of a Global IAM
Dec 04, 2019
Globalisation has spread business and production sites all over the world. Companies are faced with distributed IT systems as well as with different and demanding regulations in various countries, spanning from USA through to Europe and Asia, especially China and Russia. For many businesses IAM is a central part when it comes to managing employees, partners, customer, things and APIs in a secure and reliable way.

Event Recording
Alexei Balaganski - AI in Cybersecurity: Between Hype and Reality
Dec 04, 2019
Artificial Intelligence is surely one of the hottest topics in nearly every industry nowadays, and not without reason. Some of its practical applications have already become an integral part of our daily lives – both at home and in offices; others, like driverless cars, are expected to arrive within a few years. With AIs beating humans not just in chess, but even in public debating, surely, they’ve already matured enough to replace security analysts as well?
Event Recording
Dr. Niklas Hellemann - Next Generation Phishing – Social Engineering in Times of Voice Phishing, AI and DeepFake
Dec 04, 2019
Phishing attacks on companies have become increasingly sophisticated in recent years. The high success rates in tactics such as CEO fraud, ransomware or cryptojacking have led to hackers spending much more time and resources manipulating their targets. This is also reflected in the increased incidence of spear phishing attacks and voice phishing operations. At the same time, technological developments in the field of machine learning (e.g. in natural language processing) offer a dangerous basis for new applications in this area. Dr. Niklas Hellemann gives an overview of new social...
Event Recording
Max Heinemeyer - AI vs. AI - On The Next Paradigm Shift in Cyber Security
Dec 04, 2019
This talk intents to provide thought leadership on how AI & ML is currently being used for defensive purposes and will soon be used for offensive purposes. It covers both sides, defence and offence, and provides examples of how AI either is currently used to augment defensive measures or how AI will be used to augment cyber offence. On the defensive side we have seen an explosion in the vendor landscape using narrow AI to varying levels of success. What is undeniable is that there is improvements in blue teaming & cyber defence thanks to AI. Max will give a handful of practical...

Event Recording
Panel - The Future of AI in Cybersecurity
Dec 04, 2019
Numerous malware variants are being created daily. To adjust to this evolution, machine learning tools are being utilized by security companies to detect the novel threats and new attack vectors. Same for the threat hunting, where the ML helps in p roactively and iteratively parsing through networks detecting the advance threats. Important question is where we want to apply these advanced techniques. The technology should be applied in a smart way to tackle specific problems. In this panel we will discuss the current state of AI in cybersecurity and what the future will hold.

Event Recording
Panel - Threat Hunting: Making Data Informed Decisions
Dec 04, 2019
Event Recording
Martin Kuppinger - AI Already Revolutionizes the Way We Do Cybersecurity & IAM
Nov 28, 2019
There are many challenges business are facing when they are implementing IAM and Cybersecurity, be it role management and access controls or efficient analytics in the SOC that narrows down the incidents to put the focus of investigation on. As AI augments us increasingly in our daily live activities as well as workers on the factory floor, it also already is able to augment us in doing Identity Management and Cybersecurity better. Martin Kuppinger will look at the areas where AI already is used and where we expect AI to hep us revolutionizing the way we do Cybersecurity and IAM. He will...























