1 The Password Paradox
The research shows that 57.7% of respondents have 10 to 20 passwords in place in their organization, indicating persistent difficulties with password management. Moreover, 21.2% of users have more than 50 passwords. We expect passwordless solutions to become more popular. These statistics show that, although the passwordless market has been growing in the last few years, it has more room for growth in 2024. Looking ahead, the polls reveal that 47.1% of organizations believe that Passwordless Authentication will have the biggest impact on IAM, followed by 33.8% for Decentralized Identity.
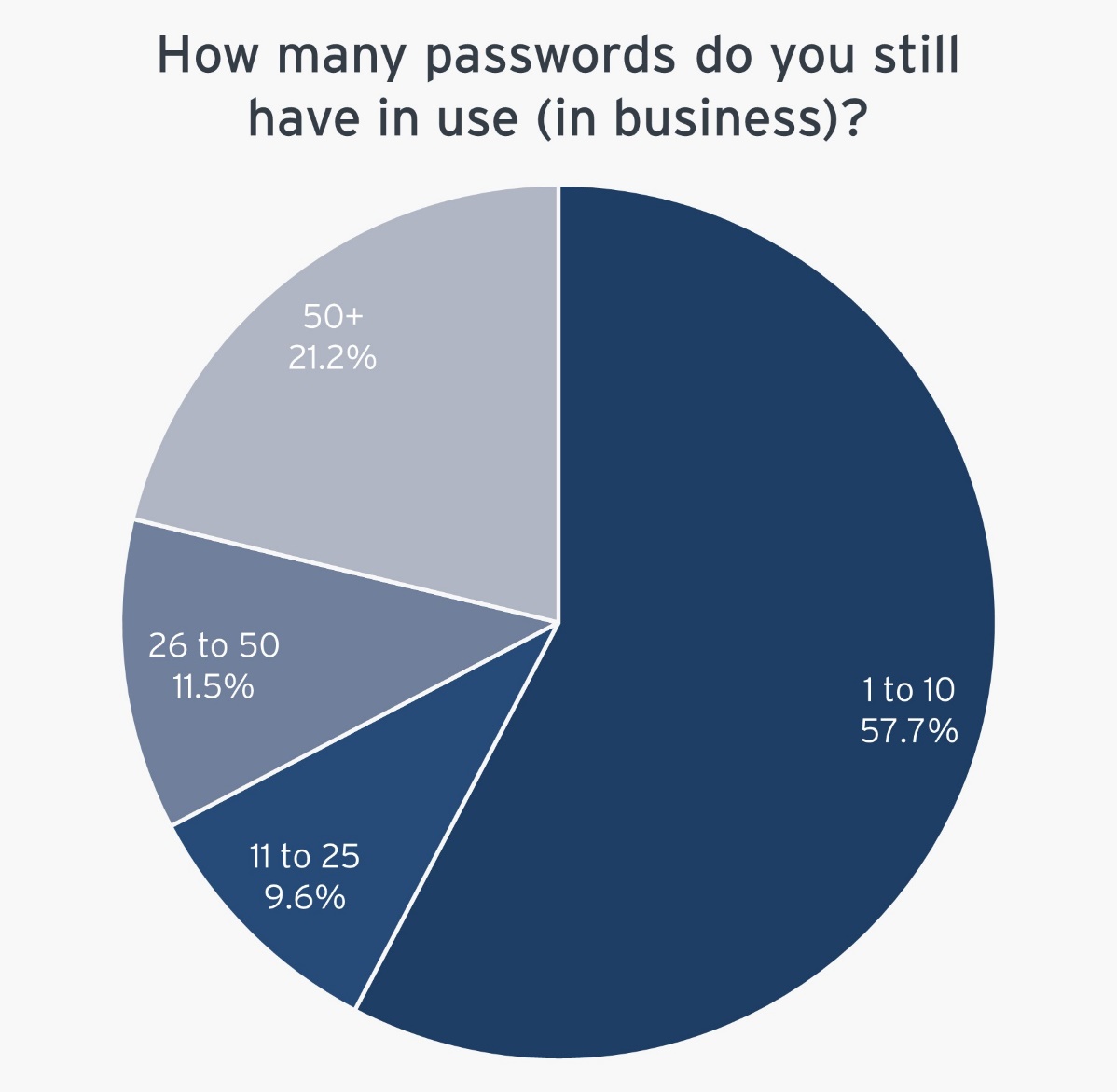
Figure 1: How many passwords do you still have in use (in business)?
2 Security Priorities
“Making Zero Trust a Reality” was ranked as the top IAM and security goal by 41.2% of participants, while “Implementing MFA/Passwordless” was ranked by 35.3%. These trends demonstrate that both Zero Trust and Passwordless Authentication technologies are mature, effectively productized in the marketplace, and are perceived as excellent investments for improving security architectures. The prominence of these two priorities also shows that most organizations have not fully rolled out Zero Trust and Passwordless.
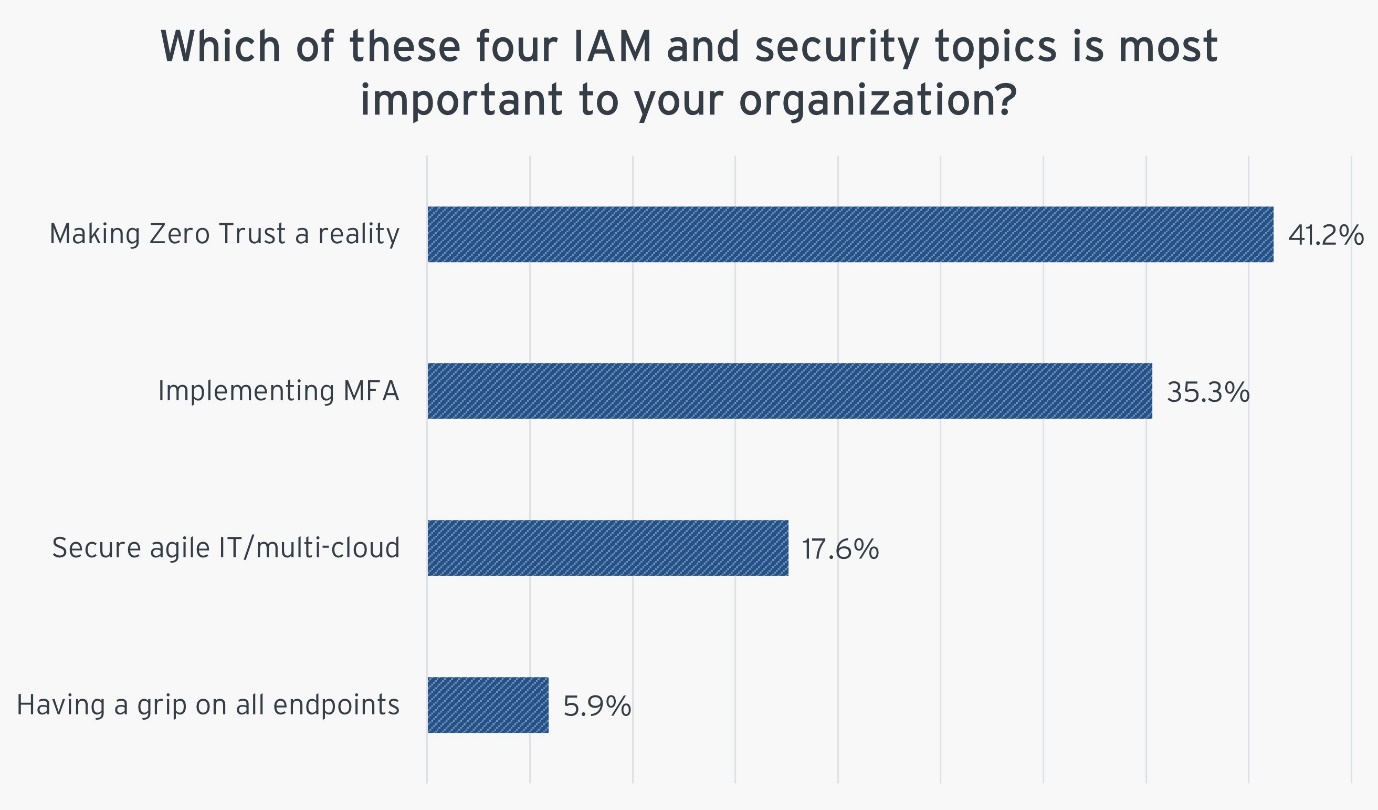
Figure 2: Which of these 4 IAM and security topics is most important to your organization?
3 The CISO and its role in organizations
The Chief Information Security Officer (CISO) reports to the Chief Information Officer (CIO) in 40% of organizations. In 34.1% of responding organizations the CISO reports directly to the CEO. This structure reflects the elevated importance of cybersecurity in corporate hierarchies. Furthermore, 43.8% of CISOs present to the board quarterly, emphasizing the growing recognition of cybersecurity at the highest levels of management.
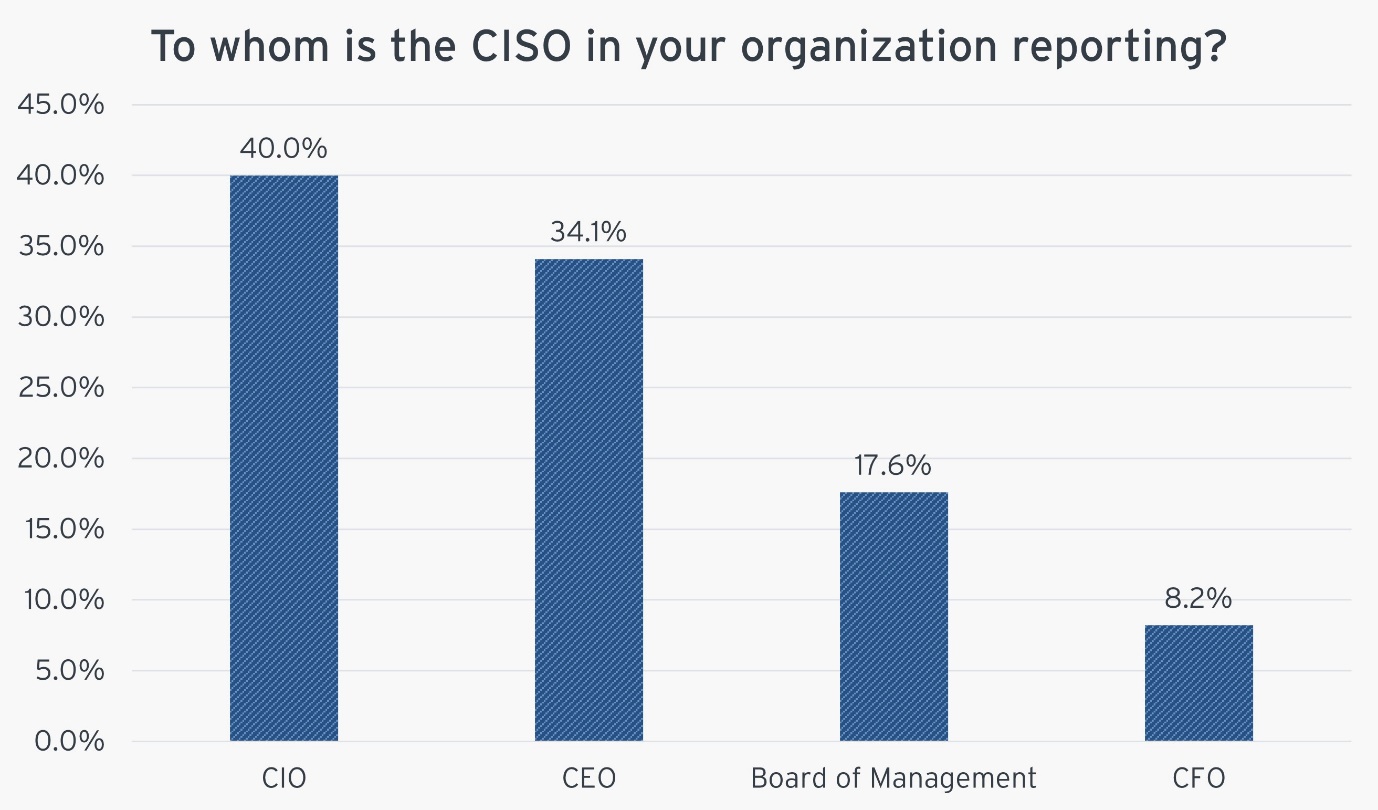
Figure 3: To whom is the CISO in your organization reporting?
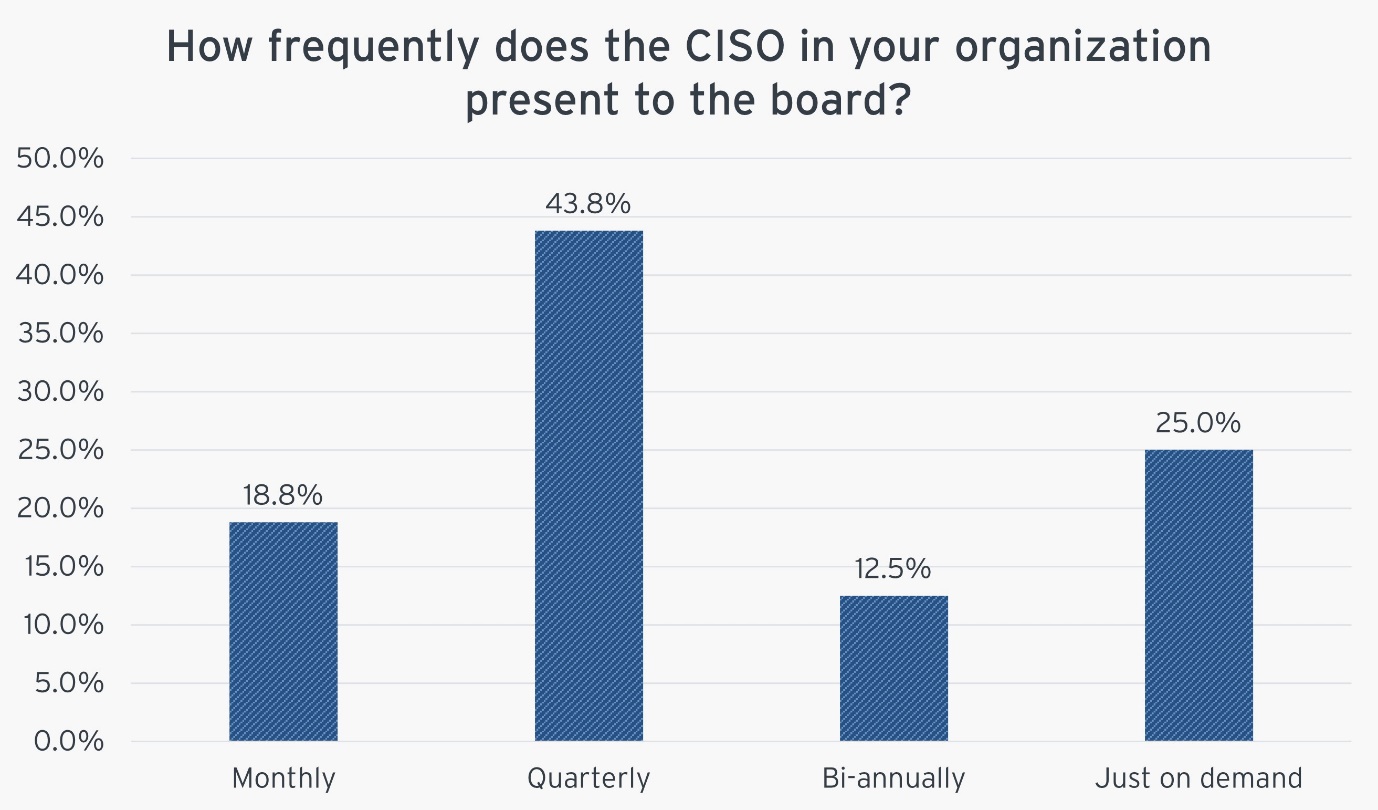
Figure 4: How frequently does the CISO in your organization present to the board?
4 Decentralized IAM Solutions
Managing identities and access permissions across multiple platforms and applications is easier with the help of unified systems. Unified IAM systems, or those that are managed identity fabrics, are essential for decreasing complexity and the administrative loads that come with running multiple distinct systems. Organizations can improve operational efficiency, lower error rates, and promote a stronger security posture by combining IAM functions. IAM solutions that are adaptable and scalable are essential as more businesses use mobile and cloud-based services.
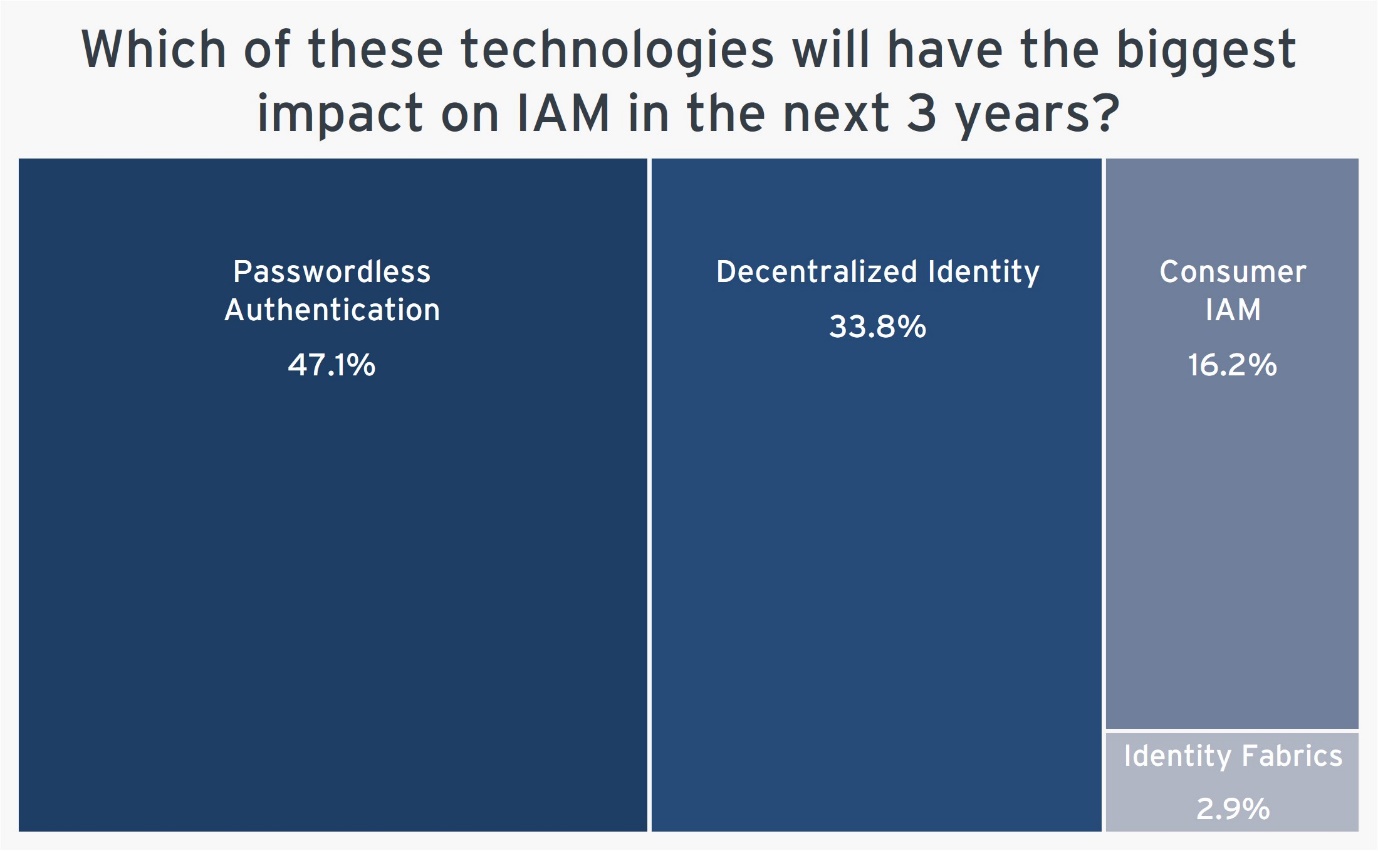
Figure 5: Which of these technologies will have the biggest impact on IAM in the next 3 years?
5 AI Became a Game Changer in IAM Solutions
There is a growing recognition of AI's potential to enhance IAM systems. However, the trend towards AI integration is more prevalent across a range of technologies and is not limited to IAM alone. Businesses are realizing AI's advantages, such as how it can automate difficult IAM tasks. This is a part of a broader trend where AI is being taken into consideration and applied to a variety of technical solutions although still under close human supervision to guarantee efficacy and handle issues like data privacy and compliance.
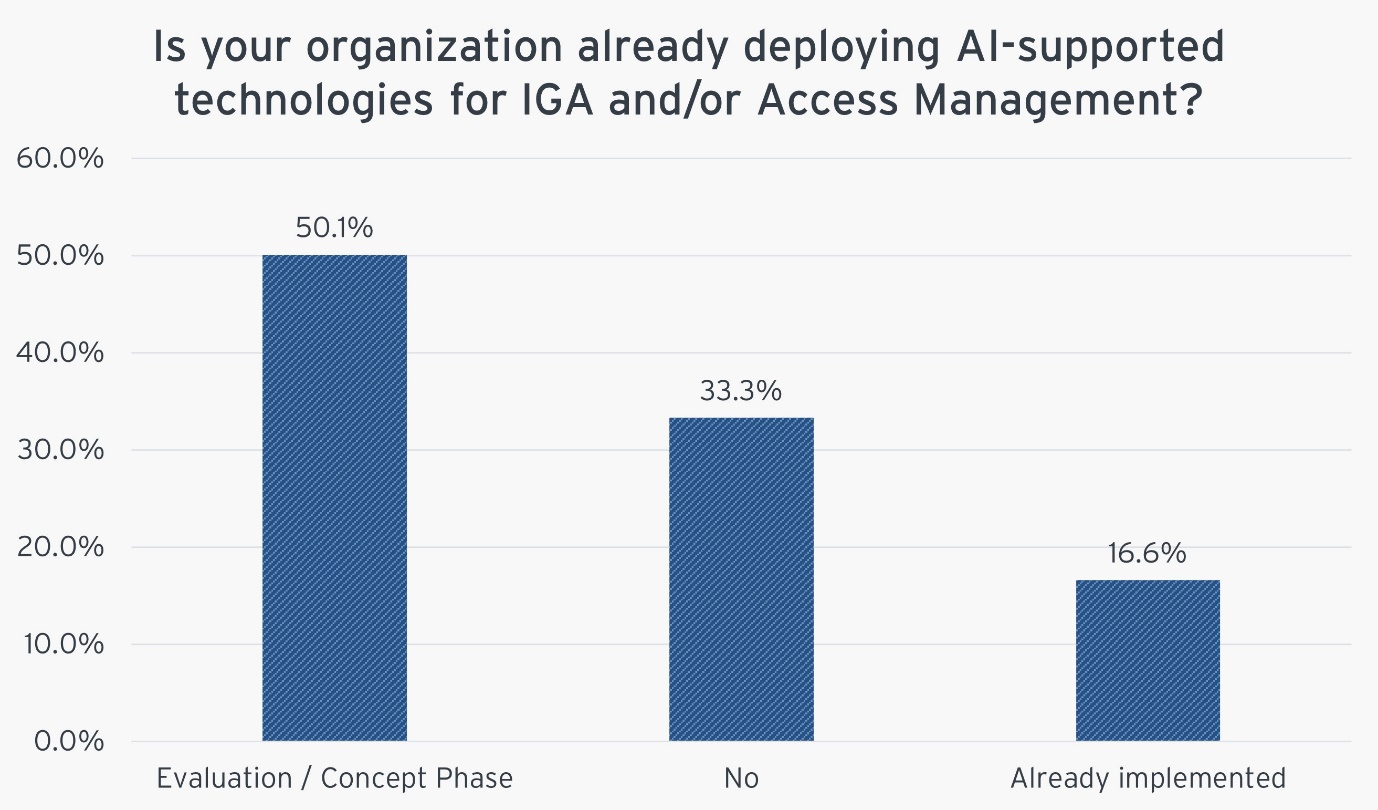
Figure 6: Is your organization already deploying AI-supported technologies for IGA and/or access management?
6 PAM Solutions
The approach to Privileged Access Management (PAM) has evolved significantly, reflecting the understanding of its critical role in cybersecurity. The data shows that different strategies are used to implement PAM systems. 16.7% of respondents are willing to switch their PAM systems, even though 37.5% of them use the same PAM platform across many departments. The variation found in PAM systems is indicative of an adaptive approach, which recognizes that various departments could have distinct security requirements and risk profiles.
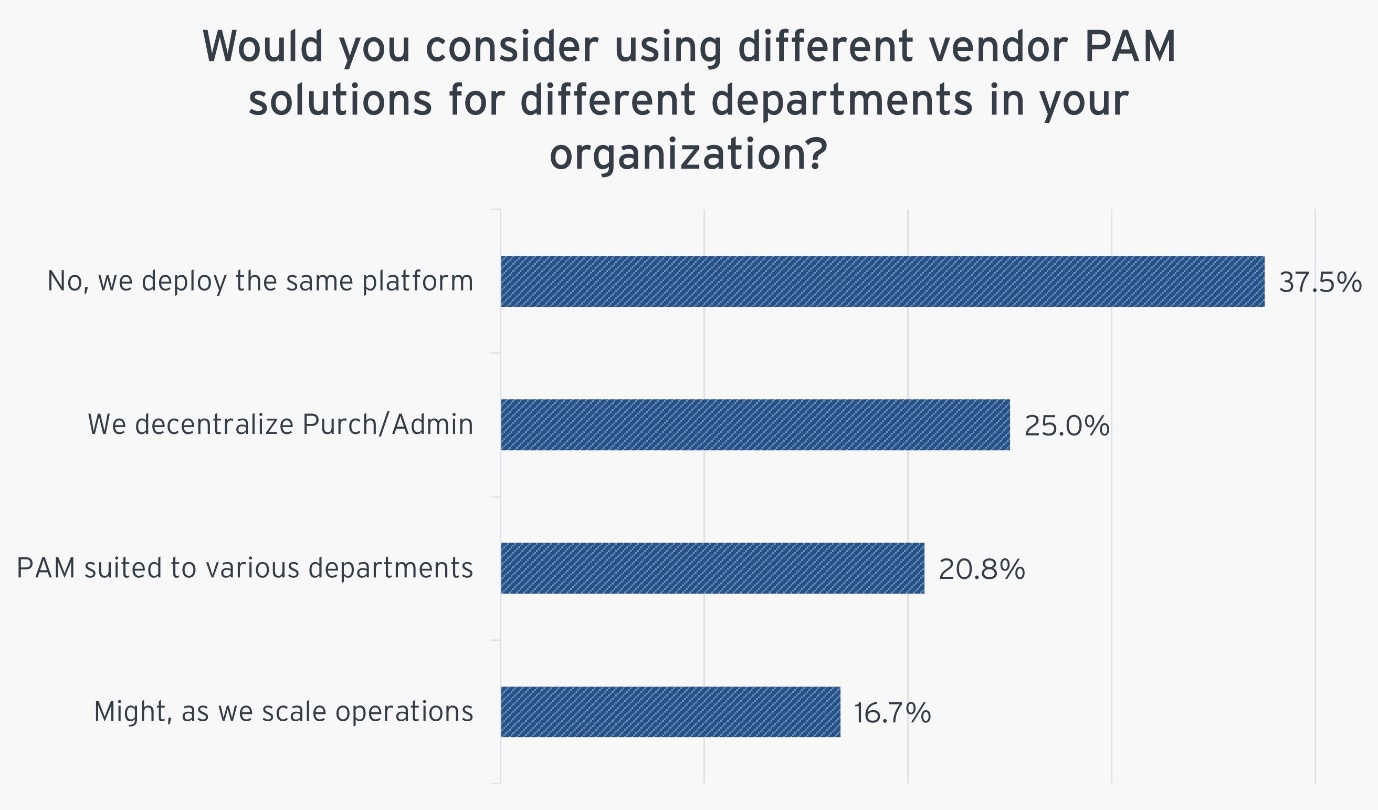
Figure 7: Would you consider using different vendor PAM solutions for different departments in your organization?
7 Conclusions
The evolution of IAM and cybersecurity in 2023 clearly highlighted an industry at a junction of innovation and adaptability. The results of our studies show that the cybersecurity landscape is changing, with organizations having to deal with issues like managing password complexity, implementing passwordless authentication and Zero Trust, and CISOs playing a more crucial role in directing organizational security strategies.
Integrated IAM solutions are becoming more popular, which indicates a strategy change that is in line with organizations' larger objectives for digital transformation. This change not only aligns with the evolving requirements of digital organizations but also helps operational efficiency and a unified security approach. In addition, the investigation of AI's function in IAM and the variety of approaches in PAM implementation demonstrate comprehension and adaptability to the complex problems associated with cybersecurity. The environment is ready for sustained growth and innovation in 2024.
In conclusion, the insights obtained in 2023 provide strong basis for the advancement of IAM solutions and cybersecurity. Future cybersecurity strategies will continue to be designed with an emphasis on integrated solutions, AI adoption, and strategic PAM deployment, making sure that businesses are better prepared to safeguard their digital assets in a world that is becoming more interconnected by the day.
8 Methodology and Sample Size
This report has been created based on accumulated results from a variety of polls that KuppingerCole ran in webinars, at events, via LinkedIn, and on other occasions during 2023.
The results are based on > 2,000 responses and have been validated by KuppingerCole analysts.
All predictions can change at any time due to a variety of reasons, including geopolitical and economic changes, innovations in the market, etc. We reserve the right to modify, update, or remove any part of this report.
The information presented in this report is intended to be for informational purposes only and is based on professional opinions derived from the analysis of survey results and interviews with software vendors, their customers, and our advisory customers.
This information is not intended to be and should not be construed as legal, financial, or professional advice. In no event will we be liable for any loss or damage including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of, or in connection with, the use of or interpretation of this report.
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.










































