1 Introduction
Integrating security into a company's digital transformation process is often challenging for organizations. If done right, it can ensure that vulnerabilities and risks do not compromise the benefits of the transformation or the company’s innovation and technological advancements. Ideally, IT security should be planned early on and maintained throughout the lifecycle of digital transformation initiatives.
Integrating identity and access management (IAM) into the IT security infrastructure is an essential first step. IAM is a framework of policies, processes, technologies, and practices organizations use to manage and secure digital identities and control access to resources. IAM ensures that the right individuals access systems, applications, data, and physical locations appropriately.
Identity Governance and Administration (IGA) is considered a subset of IAM that specifically focuses on managing and governing user identities, access rights, and the associated administrative processes within an organization. It helps organizations reduce security risks, enforce compliance with regulations, streamline administrative processes, and maintain a comprehensive view of user access across the organization's digital resources. IGA is particularly important in complex IT environments with diverse applications, systems, and user roles. Several essential components and practices of IGA include:
- Identity lifecycle management
- Provisioning and deprovisioning of access
- Access request and approval
- Access certification
- Role management
- Segregation of Duties (SoD)
- Audit and compliance
IAM and IGA are interconnected and necessary components for IT security, enabling organizations to navigate the modern digital landscape effectively. However, IGA is sometimes considered later, after IAM implementation, and becomes the last leg of security for the digital transformation journey for organizations.
Regarding IGA solutions, additional capabilities should be considered to improve process efficiencies, alleviate repetitive tasks, and reduce human error. Providing analytics capabilities to IGA can provide insights into access patterns, compliance status, and potential risks. The addition of artificial intelligence (AI), machine learning (ML) can be used to automate complex tasks. Automation within IGA can help with access provisioning when new users join the organization and the deprovisioning process when users leave or change roles. Automating these processes can help minimize the risk of orphaned accounts and unauthorized or overprovisioned access.
Another consideration for organizations is moving IT security services to the cloud and adopting cloud-native approaches to attain cost efficiency, scalability, agility, and innovation capabilities.
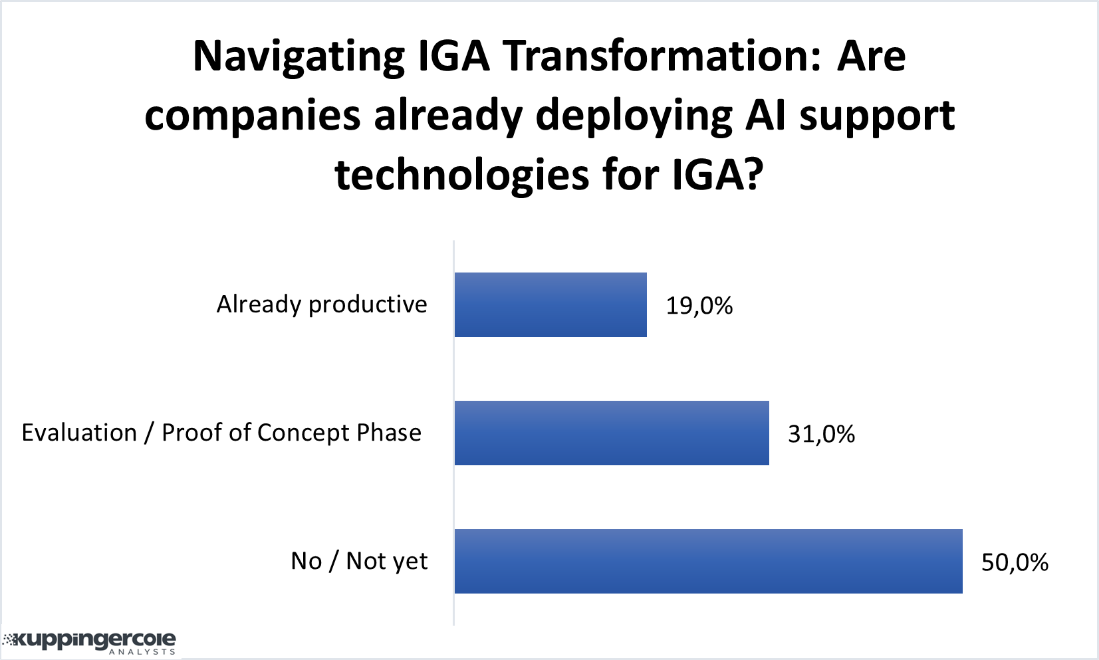
Figure 1: Data from KuppingerCole polling










































