Zero Trust is undoubtedly one of the hottest buzzwords in the IT industry. The idea that just by following a set of simple principles an organization can dramatically reduce the complexity of its IT infrastructure and significantly improve its security posture and resilience to cyberattacks is, of course, extremely appealing to everyone. Unfortunately, even the companies highly motivated to adopt Zero Trust as their new strategy are often struggling even with the initial steps.
If KuppingerCole analysts got a dollar every time we had to tell someone: “sorry, but you cannot buy Zero Trust”, we could probably all have retired early, but alas, most customers are not content with that response and would rather look for more practical recommendations. This is especially true in times when Zero Trust is sometimes presented as the only way to solve massive business-relevant problems, like quickly enabling your entire workforce to work from home because of a lockdown or protecting your business from destructive ransomware attacks.
The beauty of Zero Trust principles is in their simplicity and universality: after all, it’s just a set of several basic rules that an organization has to follow, which don’t go into technical details and are thus understandable even for non-technical stakeholders. “Never trust, always verify”, “only allow as much access as necessary”, and “monitor all activities” – that’s basically the whole of Zero Trust in a nutshell. But how do you translate them into specific technical solutions?
Well, first of all, there is no single solution that can implement it across your entire IT environment, from devices and data stores to network infrastructure and cloud platforms to applications and SaaS services. Vendors can help you with the right building blocks and general guidance, but all the critical strategic decisions have to be made by you because nobody else knows your risks, challenges, and priorities. There are however certain prerequisites that you must have in place before even starting to invest into Zero Trust products.
Start by applying Zero Trust to Zero Trust itself! Do not trust product labels and vendor claims – make sure that you always verify that their solutions actually deliver the promised capabilities and don’t have hidden limitations. You should also have an inventory of the security and other tools you already have to ensure that you do not invest into unnecessary duplication of existing functionality. And, of course, you should define your long-term strategy but make sure you can deliver regular quick wins, or your management will inevitably turn Zero Trust into Zero Budget…
At an even more basic level, the magic formula for every Zero Trust architecture is
Zero Trust = Strong Identity + Full Visibility + Policy Enforcement
The latter component is the trickiest one to implement consistently and with full coverage, but the former two you should already have in place. A robust, modern and extensible IAM system is a basic foundation not just for Zero Trust, but for any digital enterprise, and trying to implement Zero Trust without reliable identities for all users, devices and services will inevitably fail. However, for quite a few of short-term use cases, a cloud-based Identity-as-a-Service platform will work just fine, and many Zero Trust platforms actually support those (Microsoft Azure AD, Okta, etc.) out of the box.
Full visibility is also one of the basic cybersecurity hygiene principles: you can only protect what you know exists, and to protect it efficiently, you have to know what’s happening in your IT environments at any moment. At the very least, you need to collect security telemetry from endpoint devices and feed it into Zero Trust policy engines to ensure that every access decision is based on their up-to-date security posture. And again, most organizations already have tools that do exactly this – endpoint detection and response (EDR), security information and event management (SIEM) or extended detection and response (XDR). All you need is to make sure they can exchange information with your future Zero Trust solutions.
As soon as you face the challenge of actually implementing policy-based access management to any kind of sensitive resource, you’ll quickly realize that there is no one-size-fits-all approach. Securing access to web applications and, say, relational databases relies on entirely different technologies, standards, and protocols. It is up to you to decide which one you need to implement first and to find the right balance between long-term strategic projects and quick wins to please your users and management.
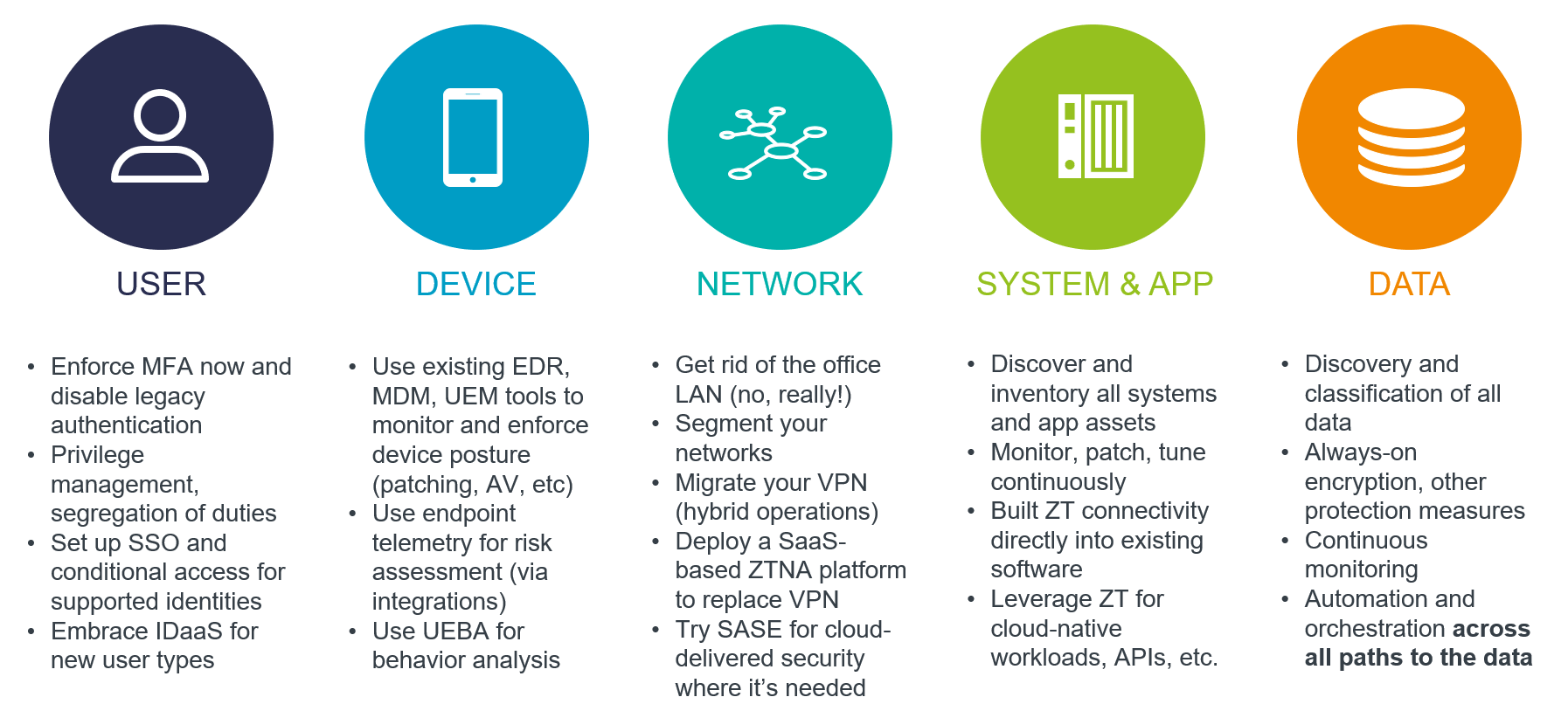
Some of those quick wins are literally quick and painless. The best example is undoubtedly Zero Trust Network Access (ZTNA). Two years of working from home have led to an explosive growth of this market, and nowadays you can find a solution for an organization of any size and industry. Some cloud-native fully managed ZTNA platforms can be deployed in minutes, and the only prerequisite is a connector to an existing identity provider. These solutions then can be seamlessly extended with cloud-delivered security capabilities to form another popular buzzword – Secure Access Service Edge (SASE).
Expanding Zero Trust to other aspects of your IT, such as cloud infrastructure and workloads, sensitive data, APIs and so on might not be as trivial, but again, the actual implementation details depend largely on your existing applications and services. Some might already ship with ZT-enabled access controls that only need to be integrated with your existing policy engine. Others might require installing third-party plugins or connectors.
If you are looking for more specific and comprehensive guidance or want to meet the real experts in the fields of identity and cybersecurity, you should definitely not miss the Cybersecurity Leadership Summit that will take place in Berlin this November. Zero Trust is one of the key topics of the summit, and we are already looking forward to interesting sessions covering anything from strategic approaches at large enterprises like Siemens or Mercedes-Benz to real-life stories of Zero Trust journeys. Whether you need a ZT 101 crash course or want to know what’s coming next in the Zero Trust evolution, our experts will have you covered. See you in Berlin!