1 Introduction
Malware is and will likely continue to be a top threat and thus a top concern among business and IT security professionals. It comes in many forms: viruses, worms, rootkits, botnets, file-less malware, ransomware, and crypto-miners are prevalent in the wild. Malware is usually, and almost by definition, an exploitation of an operating system or an application vulnerability.
Ransomware attacks are still popular and evolving. Ransomware is a form of malware that may encrypt users' data, demanding that ransom be paid for the return of control or for decryption keys. The newest forms of ransomware are deployed similarly to an APT campaign, with staging of ransomware on various machines throughout an enterprise and exfiltration of data prior to ransomware detonation. Needless to say, paying the ransom only emboldens the perpetrators and perpetuates the ransomware problem.
Moreover, in many cases the ransomware operators do not provide working decryption keys, so paying the ransom is purely a waste of money. Over the last couple of years, some attackers have used ransomware techniques and payloads for purely destructive purposes too – rather than asking for ransom, these destructive "wiper" ransomware types simply delete or zero out data. Other ransomware operators exfiltrate data and threaten to publish it unless a ransom is paid.
Once infected with ransomware, organizations must decide if they are going to:
- Pay the ransom and hope that malefactors return control, send decryption keys, or delete and not publish stolen information (not recommended since it doesn't always work and incentivizes criminals)
- Wipe affected machines and restore data from backup
- In the case of wipers, there is no choice but to rebuild from backups
Restoration is sometimes problematic if users or organizations haven't been keeping up with backups, or if backups have been contaminated by malware. Even if backups are readily available, time will be lost in cleaning up the compromised computers and restoring the data. Thus, preventing ransomware infections is preferred. However, no anti-malware product is 100% effective at prevention. It is still necessary to have good, tested backup/restore processes for cases where anti-malware fails.
Ransomware attacks often arrive as malicious links or weaponized Office docs via phishing campaigns. Disabling macros can help, but this is not universally effective since many users need to use legitimate macros. Ransomware can also come less commonly come from drive-by downloads and malvertising.
Viruses are far more sophisticated than they were decades ago. Now viruses are generally polymorphic, meaning they alter their structure to try to avoid detection upon every iteration. Viruses infect files and usually need user interaction to initiate a compromise. Worms are malicious code that spreads across unsecured networks, relying upon unpatched, compromised applications and unprotected ports. Rootkits are low-level malware usually implemented like device drivers in operating systems. Rootkits allow bad actors complete control of affected machines. Botnets are collections of controlled devices, often compromised by rootkits, that are used in large numbers to magnify other kinds of attacks, such as Distributed Denial of Service (DDoS) attacks, credential stuffing, account take-overs (ATOs), or other forms of cybercrime. Botnets can be composed of PCs, servers, smartphones, IoT devices, etc.
File-less malware is a malicious innovation that seeks to avoid signature-based anti-malware scanners by propagating between machines without being written and transferred as files. Instead, file-less malware is malicious code which spreads by process or memory injection. Once on a target device, file-less malware uses native tools like PowerShell or .NET to assemble and execute the malicious payload. File-less malware attacks are still on the rise.
All computing assets should have Endpoint Protection Detection & Response (EPDR) clients installed with up-to-date subscriptions. Windows platforms are still the most targeted, though there are increasing amounts of malware for Android. It is important to remember that Apple's iOS and Mac devices are not immune from malware, and as market share increases, particularly for Mac devices, the amount of malware for that platform will likely increase too.
EPDR solutions should be able to prevent malware execution in the vast majority of instances. In situations where compromises do happen, EPDR tools provide the ability to create alerts and reports, terminate offending processes, delete or move files, restore registries, automatically quarantine assets suspected of having been compromised, and in some cases, rollback compromised endpoints to known good states.
2 Product Description
Malwarebytes was founded in 2008 and is headquartered in Santa Clara, CA. They are a mid-stage venture-backed company originally known for their consumer antivirus and malware removal tools and have been pushing into the SMB and large enterprise markets by expanding and enhancing their products with centralized management capabilities and additional features. Malwarebytes is focused on endpoint security, with Nebula (EPDR) and Incident Response (IR) services. Malwarebytes offers managed services for their products as well.
Malwarebytes has agents for most OSes, including all versions of Windows (except Vista), Windows Server 2008+, macOS 10+, all major Linux variants, Android, and iOS 13+. The agents can co-exist with other vendors' endpoint security tools; file exclusion lists are provided to prevent software products from interfering with one another's operation. Nebula is compatible with all browsers.
Malwarebytes hosts the management console as SaaS, running in a Tier 1 cloud service provider among multiple data centers in the US. Customer incident data is retained for 90 days.
Nebula
Malwarebytes Nebula employs all major malware identification techniques such as signatures, exploit prevention, and runtime process/memory analysis. Agents have sandbox and emulator functions for testing executables; thus, Malwarebytes can operate autonomously without constant connection to Malwarebytes' cloud. Malwarebytes uses a patented ML detection model, which is transparently updated as needed.
Malwarebytes focuses on profiling "goodware" for easier detection of anomalies. The agent contains a dedicated engine for detecting ransomware-specific behavior, such as process hollowing and querying of operating systems for the presence of security software. To protect users from web-based threats, Malwarebytes employs URL filtering and IP reputation intelligence. Ads and pop-up notices can be blocked by administrative policies.
In addition to malicious code, the product looks for command and control traffic, signs of botnet activity, reconnaissance, lateral movement, and data exfiltration. Internal, open-source, and threat intelligence from VirusTotal and ReversingLabs is utilized by Nebula. Nebula parses detections, correlates signals, maps relevant telemetry to MITRE ATT&CK techniques, and assigns priorities to events for analysts.
The admin interface offers drop-down lists and accepts regular expression input for query building. Dashboards show endpoint list views, detections, timelines, and process graphs. Remediation actions are recommended, and response actions can be scripted and applied across all nodes. The "Flight Recorder" feature allows activity recording for later analysis. Nebula has integrations with Palo Alto XSOAR and Splunk Phantom, which allow management and playbook execution from those SOAR platforms.
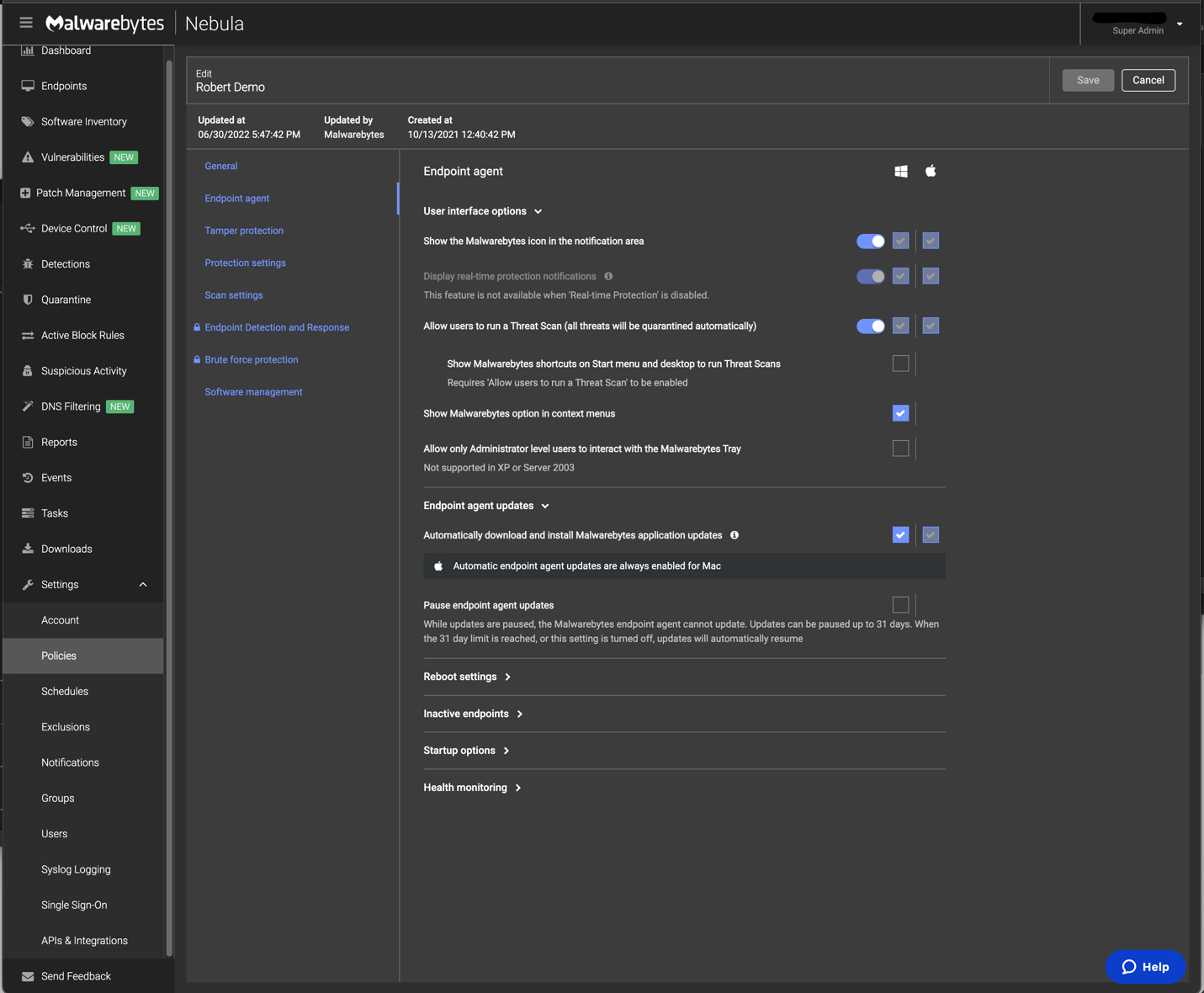
Customer admins are alerted to suspicious events via email, SMS, Slack, and any Webhooks-based service. Malwarebytes supports syslog for forwarding telemetry to SIEM systems, and custom parsers are available for IBM QRadar, Rapid7, and Splunk. Response actions, which must be manually invoked unless remotely managed via the above-mentioned SOAR tools, include process termination, host isolation, file quarantine, rollback of registry and file changes, and full node rollback up to 72 hours. Malwarebytes can integrate with ServiceNow ITSM for enterprise management.
Customer admin access to their management console instances can be protected by OTP authentication, and SAML is supported for identity federation. Various roles for different levels of administrative access are present in the management console.
Incident Response
Malwarebytes' Incident Response product adds incident response capabilities on top of their Nebula EPDR offering. It can be used as an add-on working in conjunction with other vendors' EPDR products.
As mentioned above, EPP agents aim to prevent initial malware infections. Malware sometimes evades detection using sophisticated means. Many EDR tools allow coarse-grained remediation by terminating offending processes, deleting known malware files, and restoring endpoints to prior configuration snapshots in the attempt to get back to an earlier state before the endpoints were infected. Most such solutions rely on the Volume Shadow Service in Microsoft Windows for this capability.
Rolling back to previous snapshots can be problematic for two reasons. Recent changes to configurations, applications, and data will likely be lost in the process. If a recent VSS snapshot can be used, there may be only insignificant differences and few objects lost. If older snapshots must be used, then a greater amount of data will be lost. In either case, productivity is adversely impacted. Secondly, it can be difficult to determine precisely when malware first infiltrates an environment, and to what past point affected systems should be restored.
State actors behind Advanced Persistent Threat (APT) campaigns often silently gain a foothold in their targeted environments weeks or months ahead of beginning lateral movement and reconnaissance activities. Moreover, some cybercriminal groups who facilitate or perpetrate ransomware attacks have begun using the same slow movement tactics as APT actors, meaning that ransomware could be surreptitiously staged on victim devices days or weeks before it is detonated.
Malwarebytes' Incident Response provides remediation functions including the detection of Potentially Unwanted Modifications (PUMs) and Potentially Unwanted Programs (PUPs), and granular removal of malware compromise artifacts. PUPs are programs that often come bundled with other software that users download and may contain "toolbars", directed search capabilities, ads, and pop-ups. PUPs are "grayware"; that is, PUPs are not necessarily malicious, but can waste computing resources and deliver unintended results to users. However, PUPs can become a vector of attack for unscrupulous threat actors, and business risks should be weighed carefully.
Examples of malware artifacts that Incident Response can discover and eliminate include:
- Files
- Registry entries
- System drivers
- Memory objects, including in-memory threading (orphaned processes)
- Startup objects
Malwarebytes Incident Response can work in agentless mode with 3rd-party EPDR products. Malwarebytes leverages APIs to inject Incident Response code into the process of the EPDR product. Thus, Malwarebytes Breach Remediation (MBBR) runs in the context of the EPDR solution, with the requisite system-level privileges to expunge malware and its attendant artifacts. MBBR can throttle its CPU usage up and down so as not to impact users.
The full Incident Response agent has a small memory footprint. Malwarebytes' complete EDR package can be enabled from MBBR if customers decide to upgrade, making it easy for those without EDR solutions to deploy it.
Malwarebytes Remediation
Various approaches to malware remediation exist across the different products in the field. When typical remediation tools attempt to remove malware, they focus primarily on the discovered actively malicious executable. But there are often collateral system changes that conventional remediation techniques do not address. These residual changes may leave the endpoint vulnerable to rapid reinfection or, in the worst case, leave the endpoint in a dysfunctional state.
Malwarebytes remediation engine (Linking Engine) uses a signatureless heuristic algorithm and information about common malware behavior to identify and remove associated components related to the specific type of infection. It will identify the system changes associated with or generated by the active malicious executable to thoroughly remove the infection and return endpoints to healthy states.
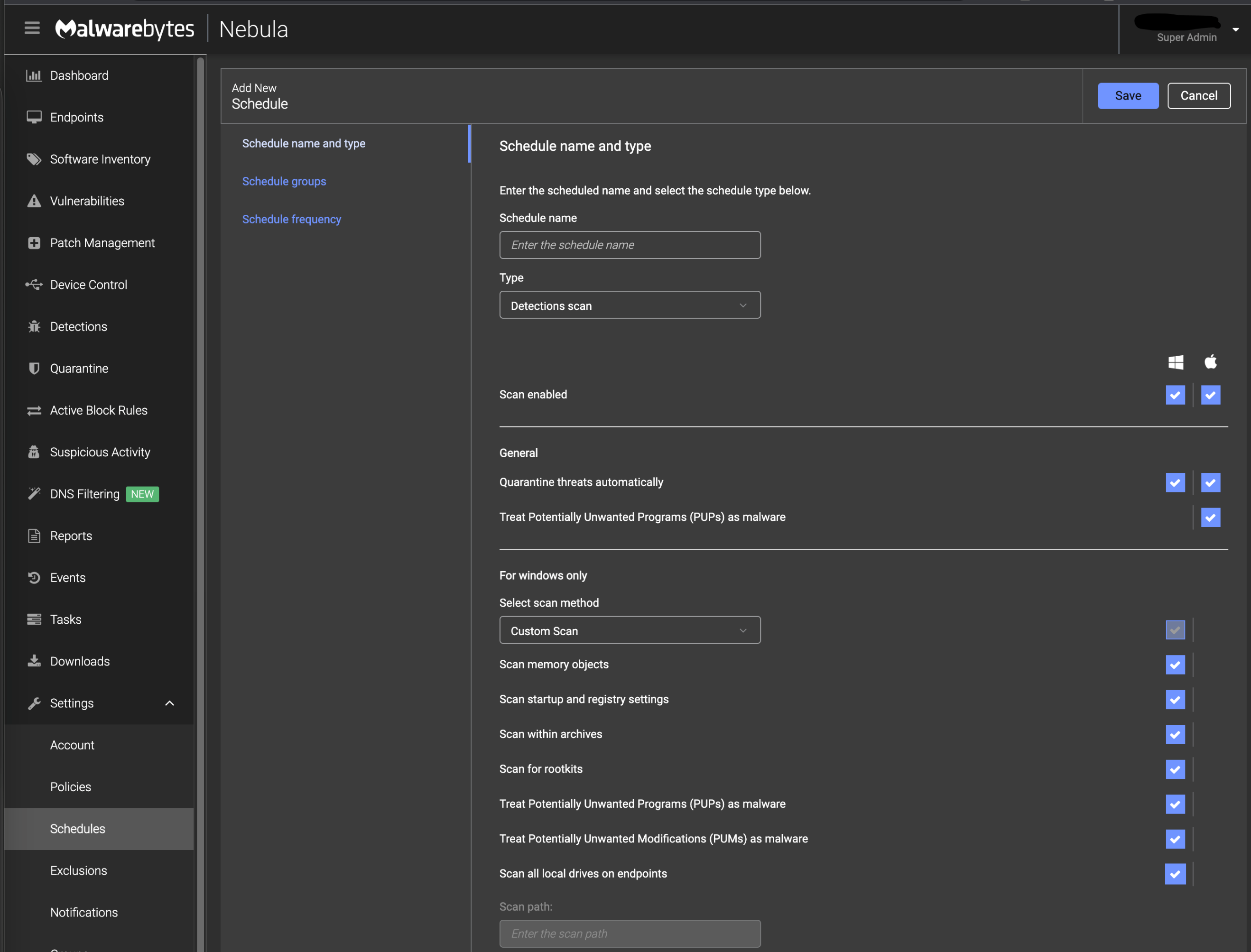
Malwarebytes also provides API connectors for other vendors' EPDR solutions to integrate with its IR.
3 Strengths and Challenges
Malwarebytes Nebula provides good malware identification capabilities at the endpoint and has agents for the most common operating systems in use today. Nebula uses a good mix of pre-execution and runtime scanning methods powered by Machine Learning detection models. Nebula would benefit by adding a few functions, such as application controls and system file integrity monitoring.
Malwarebytes Incident Response enables customers to clean up after malware infections more completely and yet selectively. While many EPDR solutions allow system rollbacks (leveraging the Windows VSS) to previous snapshots, Malwarebytes Incident Response can more granularly extract malware and its artifacts, such as registry entries and startup objects. This method can often avoid data and productivity losses encountered by the more coarse-grained system rollback approach.
Malwarebytes IR is leveraged via RESTful APIs for integration. Packaged connectors for other security tools would make the solution even more extensible. Malwarebytes does provide sample integrations of IR for SOAR platforms like Splunk SOAR (formerly Phantom) and Palo Alto Networks' Cortex XSOAR.
Enterprises are increasingly interested in security incident response capabilities that facilitate remote operations. Most enterprises have not only multiple sites but a growing and likely permanent remote workforce, which means that malware detection and remediation tools need to be effective even when technicians cannot physically interact with compromised computing assets. Support for relevant threat intelligence standards and additional automation would be helpful.
| Strengths |
|
| Challenges |
|
4 Related Research
Leadership Compass: Endpoint Protection Detection & Response
Market Compass: Endpoint Protection Detection & Response
Leadership Brief: Do I Need Endpoint Detection & Response?
5 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.