1 Introduction
Dynamic Authorization Management, sometimes called Entitlement Management, is a superset of the Attribute-Based Access Control (ABAC) sector and is arguably the most exciting area of Identity and Access Management (IAM) today. It is the way in which organizations can leverage their identity and access management environment to manage access to restricted resources.
The ABAC model is more flexible than RBAC and can even be used to emulate (and extend) RBAC. Although it is easy to express and maintain business policies using it, moving towards ABAC requires a new understanding of how to deal with authorizations, compared to the well understood RBAC approach. But it provides more flexibility and tighter integration with applications.
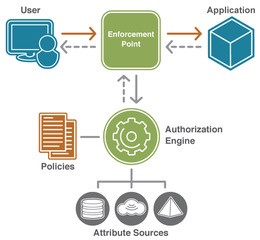
In a typical Dynamic Authorization Management infrastructure deployment, there are five main components:
Policy Decision Point (PDP) – a service that evaluates access requests against authorization policies and responds with a Permit, Deny Not applicable or Indeterminate decision
Policy Administration Point (PAP) – a facility to generate and modify policies
Policy Retrieval Point (PRP) – the location where policies are stored
Policy Information Point (PIP) –the data store of attributes by which decisions are made
Policy Enforcement Point (PEP) – a service that sends an access request to the PDP and enforces its decision.
Using this Dynamic Authorization Management model, access control to APIs, microservices, and other application resources can now be made in real-time by policies in a centrally-managed “decision point”, using attributes such as a user id as a subject, a resource type to be accessed, allowed actions on a given resource, or an environmental context such as the time-of-day. The benefits are significant: authorization is externalized, access policies become centralized, and software development is simplified. By externalizing access control decisions, business management is improved, and costs are reduced.
The Axiomatics Policy Server (APS) provides a fully featured solution for companies wanting to provide fine-grained access control to protected resources such as APIs, microservices, and documents.
Axiomatics was founded in 2006 and is headquartered in Stockholm, Sweden with offices in the U.S. Their customers include Global Fortune 1000 companies and federal government agencies and ministries.











































