We know that the way forward for business IT is to use multi-hybrid architectures for long term agility of operations. Such architectures will include multiple clouds for new services, on-prem stacks, edge devices, OT integration and much more. But while the need for multi-hybrid is clear, the resulting complexity of ad hoc deployment of multi-hybrid architectures can lead to serious security holes.
Unmanaged complexity will invariably result in an enlarged attack surface that will encourage attackers to take a pick and mix approach to find and exploit vulnerabilities within your operating environment. Attackers will find holes to deposit new malware or ransomware and then mix these with malicious tools that they may already be deploying on your networks – all without your knowledge. Unlike the Pick ‘n’ Mix counter at the sweetshop, such malign confectionery will taste sweet only to the attackers.
So why don’t we just make everything simpler?
Good point, and we will get to that but unless your organization was built yesterday, from the ground up, with a cloud native architecture that so far does not extend much beyond your own employees – a kind of cloud first perimetered structure, it is likely your IT stacks will be complex and challenging to audit and manage as part of a multi-hybrid architecture.
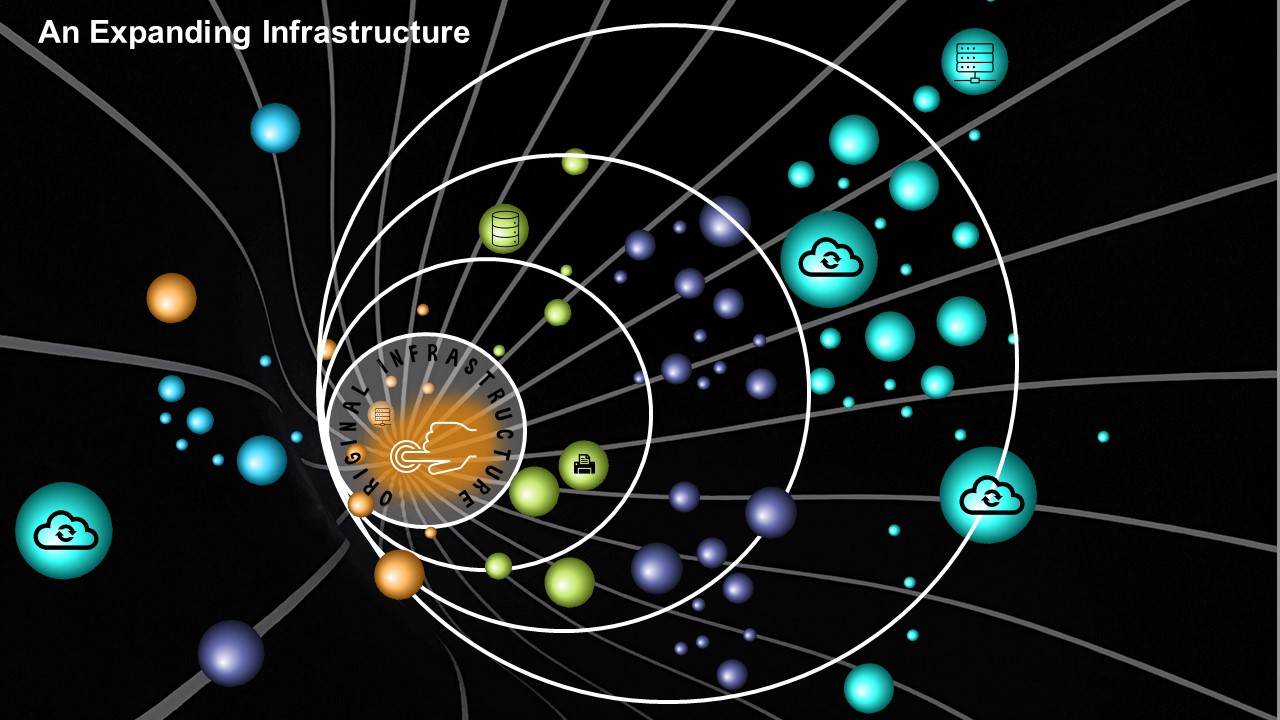
Figure 1: An expanding infrastructure will inexorably get more complex as it grows beyond its original state. The spheres represent resources such as multi-clouds, on premise stacks, databases, date centres, tools and applications etc. The swirling dots represent machine and human identities (Source: KuppingerCole).
No, like the Universe, today’s typical IT infrastructure is constantly expanding as demand shifts and change and unplanned and unsanctioned mini galaxies are created in the form of clouds purchased at departmental level and DevOps groups, among others.
Because, of course, IT is complex, it’s a fact – even that seemingly simple cloud native architecture will take trained and qualified people to construct – and the same level of expertise to maintain. Now consider the more typical scenario that we see every day. Older organizations will consist of the old and the new – usually not working together in perfect harmony. There will be (possibly) old mainframes, legacy stacks on premises, private clouds, public clouds, third party networks, remote workers, endpoint devices, edge devices, IOT, unauthorised devices and more.
And of course, within all that will be the reason why the architecture can be become a deadly attack surface. It’s all those identities – your people, your devices - flowing in and around the architecture looking for access to services, applications and more. And this is key. If IT ran without identities acting with agency, then the attack surface would be minimal. Unfortunately, nothing can be created, nothing can be done without human and machine identities doing something and using applications.
Our new multi-hybrid world is geared expressly around the notion that the quicker employees and others get access to resources, the more efficient the business will be and the more competitive – and this is mostly true is the IT architecture is engineered well. But multi layered IT stacks engineered for a business outcome will not solve the security and risk equations the architecture poses on its own. IT architecture can only be simple to a certain degree so we need to look at how organizations can simplify the policies and processes needed for the business outcome and harden the identity and access management protocols. For this, organizations need to take their own pick and mix approach to the stuff happening inside their multi-hybrid infrastructure.
So, how to simplify what happens within the multi-hybrid infrastructure.
First off, this is not a quick process and trying to outline every step you should take to reduce your attack surface in a multi-hybrid infrastructure is impossible in a blog, but we can do themes and high-level options. And of course, KuppingerCole analysts are always available for advisory services on digital transformation.
In short, you need to reduce complexity by focusing on processes and outcomes – mostly around managing identities and access to resources. The chart below, by KuppingerCole’s Principal Analyst, Martin Kuppinger, shows at least some options that may be useful to an organization created in that way. But this is just one example, every organization – yours most importantly – will be different. Your universe will be expanding in different ways – you may be running AWS but you may not use VMs. You may process financial information, but you don’t use edge devices or IoT. And so on, bearing in mind that may all change in the future.
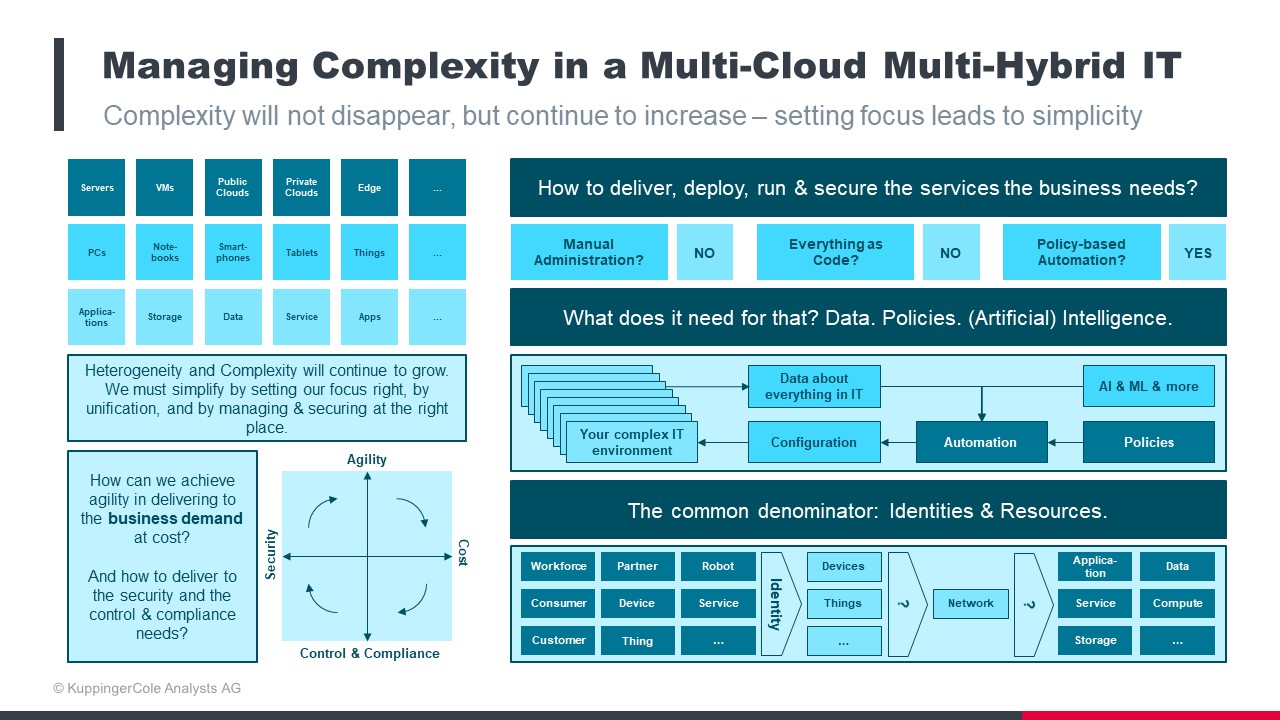
Figure 2: How to start thinking about managing complexity in multi-hybrid environments.
Therefore, before you can simplify operations inside your infrastructure the three key questions to ask are:
- What is the desired outcome? How can you deliver, run and secure the services the business needs?
- What are the components in your IT environment needed to deliver that outcome? Look at what makes up your infrastructure, the data, the applications, and the policies that control usage.
- Who or what needs access to those components? Choose from data, people, machine identities, third parties, digital things, devices etc.
So that’s a very simple chart we have created to illustrate what, in reality, looks more like the expanding universe infrastructure in the first diagram. But it’s a start and one that will focus minds on reducing complexity within, and from a user identity viewpoint – that is critical. You need to reduce vulnerability from identity management failings and determine how a complex environment can be made simpler and reduce the attack surface at the same time.
A Pick ‘n’ Mix mentality should be something that works for you – you choose what you need, who gets access to what and what the outcome is. This is good, but without rationalising identities and access management within and outside of your multi-hybrid architecture, you will never overcome the inevitable complexity of the physical architecture because you have no view on what is happening across it. And it will reduce the risk of attackers picking unmanaged identities to find their way in across your multi-hybrid infrastructure.











































