A new strain of Sodinokibi ransomware is being used against companies in the United States and Europe. Already notable for a steep increase in ransoms demanded ($500,000 on average), the malware can now activate itself, bypassing the need for services users to click a phishing link for example. In addition, the Financial Times reports that criminals are targeting Managed Service Providers (MSPs) to find backdoors into their client’s data, as well as attacking companies directly. “They are getting into an administration system, finding lists of client privileged credentials and then installing Sodinokibi on all the clients’ systems,” the report warns.
Ransomware has proven to be highly effective for cyber criminals, as many companies have no alternative but to pay up after they have been locked out of their own systems. This is particularly true of smaller companies who often have no cyber insurance to cover their losses. Criminal hackers have also become more ruthless – sometimes refusing to unlock systems even after the ransom has been paid.
But the sophistication of this new strain of Sodinokibi and the inflated ransom demands tells us that the criminal developers and distributors have raised the bar. The ransomware does not need to find vulnerabilities, as it gains “legitimate” access to data through stolen credentials. Left unchecked, Sodinokibi threatens to be as damaging as its notorious predecessor, Petya.
Even Managed Security Service Providers (MSSPs) are not immune. According to reports, one such MSSP was attacked through an unpatched version of the Webroot Management Console, enabling attackers to spread the ransomware to all its clients. Webroot responded by sending out a warning email to all its customers, saying it had logged out everyone and activated mandatory two-factor authentication.
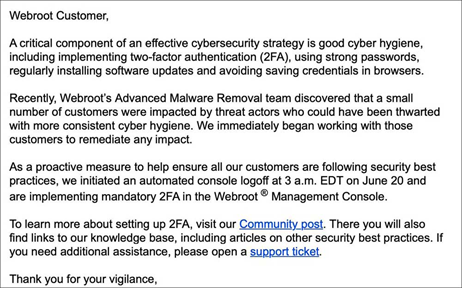
Webroot’s warning email after one of its MSSP customers was attacked by Sodinikobi
Notwithstanding the fact that any MSSP clients should expect them to take robust and regular proactive security steps as part of an SLA, it shows that diligent use of IAM and authentication controls can do much to prevent ransomware from doing its worse. But it is privileged accounts that are the true nectar for cyber criminals as these unlock so many doors to critical data and services. Which is why PAM (Privileged Account Management) is essential in today’s complex, hybrid organizations and if this responsibility is outsourced to MSP or MSSPs it is doubly important. (For more on PAM please see our recent Leadership Compass and Whitepaper research documents).
The success of any ransomware, which is not a complex piece of code in itself, depends on the lack of preparedness by organizations, and a lack of due diligence on patching systems to prevent it reaching its intended targets. In the case of Sodinikobi, it’s new ability to execute unaided makes this more important than ever.
When too many users have access to critical data and systems, it makes life much easier for ransomware. A properly configured and up to date PAM platform, either on premises or at an MSP will do much to stop this and prevent the situation found at many organizations where Privileged Account and Admins often have too much access. Best practice for today’s enterprise environments is to set credentials for single tasks and be strictly time limited - and setting two-factor authentication as default for privileged accounts. This would stop ransomware from spreading too far into an organization. Another nice concept for MSPs and MSSPs is fully automated administration of client services with well tested runbooks, and no personalized access to the systems at all.
Of course, a management platform should be patched to stop any form of ransomware reaching those credentials in the first place - patches for Sodinikobo are widely available – but as we have seen organizations cannot rely on that to happen. Given what happened with the WebRoot platform there is a strong argument for organizations to host IAM on premises, at least for privileged account management so that they have control over patch management. A robust IAM and PAM solution will prevent “access creep” by ensuring the consistent application of rules and policies across an organization. After all, hackers can’t demand a ransom if they can’t get access to your critical systems.













































