Identity and Authentication
Digital transformation can be defined as a process that organizations go through to deliver digital services to their customers and consumers in the Digital Age. Essentially, delivering digital services requires the management of the digital identities of consumers, customers, and business partners in a secure and seamless manner. Therefore, the success of digital transformation initiatives depends on managing access and managing these digital identities.
In contrast to the increased centralization of digital identity, the authentication layer has become more complex and fragmented. However, it's important to understand the difference between identity and authentication before we get into passwordless authentication. Identity is who you are. Identity proofing is about knowing whether someone is who he or she claims to be. It's the process of verifying the identity of users based on life history, biometrics, and other factors before granting them access to an application or system.
On the other hand, authentication is an ongoing identity-proofing process that ensures both the identity of digital users and the integrity of their devices. Nevertheless, disruptive login experiences and the continued reliance on passwords are creating significant challenges for consumers and enterprises. As a result, organizations are starting to adopt new authentication mechanisms that go beyond the traditional username and password. This passwordless approach leverages public-key encryption and open standards to offer greater flexibility and increase both security and convenience.
The Birth of Passwordless
In today's digital world, identity theft and credential-based attacks are some of the most pressing concerns for companies and consumers alike. For years, the use of passwords as the primary method of authentication has made identity a nuisance in the digital world. Since data breaches are often the result of stolen credentials and compromised passwords, organizations are looking to adopt more modern forms of authentication that can help close the security gaps that are associated with the use of passwords.
As a result of the security risks and inconvenience of passwords, businesses and organizations are starting to embrace passwordless authentication technologies. The evolution of passwordless was driven by the adoption of multi-factor authentication (MFA) and Single sign-on (SSO). The combination of these two technologies, coupled with the exponential growth in smartphone use and the development of open standards such as FIDO2 and WebAuthn has further generated adoption of passwordless systems.
Legacy MFA solutions were supposed to solve the problem with passwords, but these still rely on the password as a backup or first factor of authentication. MFA requires users to provide two or more factors in order to be authenticated: something they are, something they have, and something they know. Unfortunately, some of these factors are prone to phishing attacks, such as mobile SMS codes, voice calls, push notifications, and one-time passcodes (OTP).
SSO is an authentication method that allows a user to enter one set of login credentials (such as name and password) in order to access multiple applications. With an SSO mechanism in place, users only need to authenticate themselves once regardless of which applications or websites they access. While SSO can be paired with password-based authentication, integrating it with passwordless access is the key to unlocking its full potential.
Separating Authentication from Identity
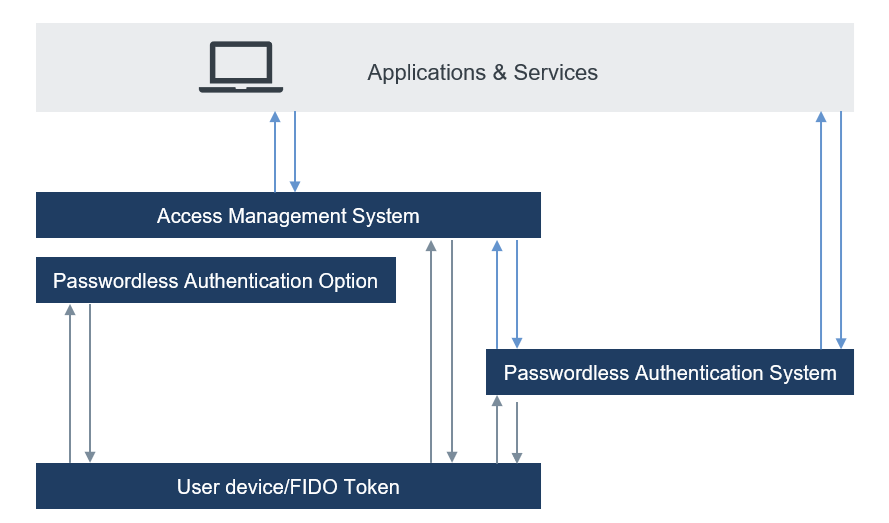
Organizations must choose between adopting a single identity platform or maintaining multiple fragmented identity systems as they move to the cloud. The separation of authentication from identity providers is being implemented by businesses and organizations in order to fully leverage passwordless technologies. It is important for passwordless technologies to have a passwordless authentication layer in front of the various access management systems.
Passwordless authentication should work across everything –all attack surfaces and identity sources, apps and devices, the VPN, SSO, Azure AD, operating systems, workspaces, servers, and whatever your organization has in place. Some solutions in the market are using passwordless at the device, and then federating to other access management services or directly into applications.
Separating identity and authentication is a very important thing. If implemented successfully, organizations will provide their users with a frictionless user experience and a consistent authentication approach. In addition, IT teams will no longer be overburdened with managing multiple identity and MFA products. Thus, fully leveraging the potential of passwordless technologies.