In their race towards digital transformation, organizations are using cloud services to accelerate the development of new apps and improve efficiency. They allow new applications to be rapidly developed, existing applications to be modernized and deployed without additional capital spend. This provides important business benefits but also increases the challenges for the cloud customer to ensure cyber-security and regulatory compliance. It is in this light that the recent announcements from GCP (Google Cloud Platform) need to be understood.
Trust but Verify
Initially, cloud service users were concerned that they had no control over the way in which the services themselves were managed and secured. The major CSPs (Cloud Service Providers) now go to great lengths to secure the infrastructure of their environments and it has become clear that many of the cloud security challenges lie with the customers’ own use of these services. For example, security and compliance are often outside the skills of DevOps teams or are overlooked and this can lead to the existence of critical vulnerabilities that can be exploited by cyber adversaries.
An additional concern is the risk of government interference in the operation of the service or demands for access to the data it holds. This concern was recently rekindled with the EU Court of Justice Ruling on the EU-US Privacy Shield.
The onus is on the CSP to gain customers' trust in all of these areas.
GCP publish an Enterprise Data Transparency Report that identifies the number of government requests received for Google Cloud Platform and G Suite Enterprise Cloud customer. This report claims that a very small percentage of requests were for enterprise data and that Google did not produce any GCP Enterprise Cloud customer data in response to government requests.
The customer always needs to verify the claims of the CSP. SLAs provide some reassurance but usually with limited recourse if they are missed. Contracts are usually written by the CSP and are not negotiable. Independent certification of compliance is useful to provide a snapshot in time. The best verification is proof that the service was designed, implemented, and is run with security and compliance built-in.
Securing Data and Access
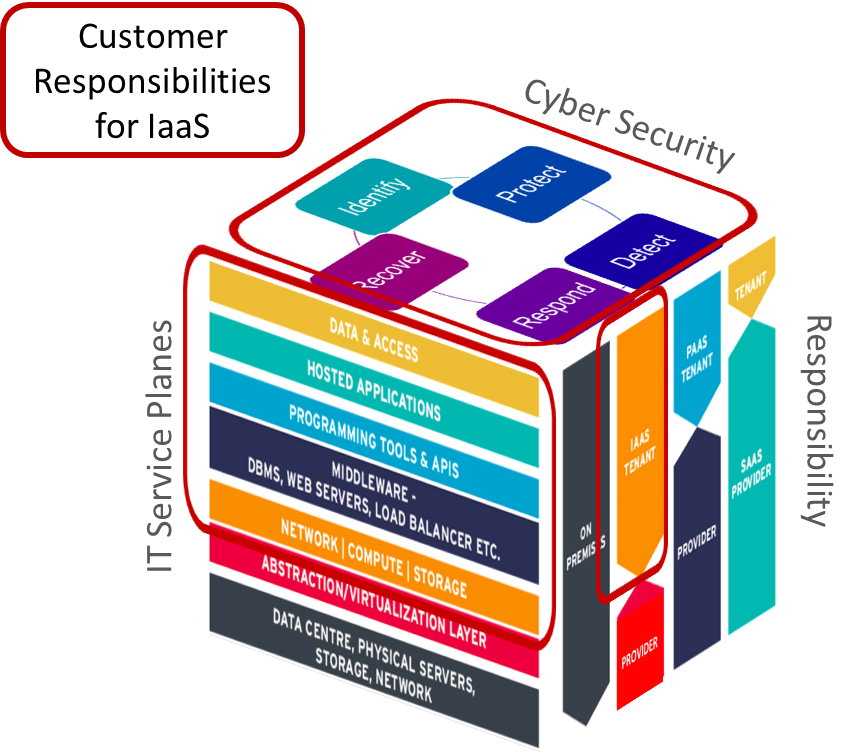
When an organization uses a cloud service the responsibility for security and compliance is shared (see graphic). It is always up to the customer to classify the data that they hold in the service and to control access to this data according to the risks and their compliance obligations. The CSP must secure the infrastructure and should provide the capabilities for the customer to assess and control their use of the service.
One critical control for this is data encryption – however, customers need to consider which form of encryption is appropriate for their risks. For example, while data may be encrypted during transit on the network and at rest in the database and - this will protect against interception and media loss, but it does not protect against application-level attacks such as SQL Injection.
GCP already provides the customer with the capabilities to encrypt their data and to manage their own encryption keys. This includes a cloud-hosted key management service that lets the customer manage their cryptographic keys for their cloud services the same way as on-premises. It also provides HSM as a service to provide hardware protection of the keys. Additionally, in beta is Key Access Justifications a capability that gives the customer visibility into every request for an encryption key, a justification for that request, and a mechanism to approve or deny decryption in the context of that request.
Confidential Computing
While data is being processed in the customer’s applications it needs to be decrypted. This creates a small but important risk to confidentiality through RAM scraping attacks for example. Intel SGX technology already enables applications to be written to process data within protected enclaves. However, this typically requires development changes to the application. GCP Confidential Computing (in beta) is a technology that encrypts data in-use while it is being processed. Confidential Computing environments keep data encrypted in memory and elsewhere outside the central processing unit (CPU). Google claims that this can be implemented at a VM level without any need for code changes at the click of a button.
Assured Workloads for Government
Normally CSPs offer cloud services tailored to the specific compliance requirements of governments. Often, these are hosted in dedicated data centres and managed by government accredited staff to ensure compliance. However, this slows the deployment of new features and does not scale to support other highly regulated industries such as finance. In response to this GCP has announced Assured Workloads for Government. Google claim that this will allow them to support US Government workloads to IL4 within their normal infrastructure by:
- Automatic enforcement of data location: to meet U.S. government compliance requirements by choosing to store data at rest in U.S. regions.
- Personnel access: to limit Google support personnel access based on predefined attributes such as citizenship, a particular geographical access location, and background checks.
- Built-in security controls: to reduce the risk of accidental misconfigurations by choosing from available platform security configurations.
- Automatic enforcement of product deployment location based on organizational policy.
Certificate Authority Service
Digital certificates underpin identity and authentication for many networked devices and services. This is not new technology but is becoming more important as a mechanism to securely identify IoT devices. However, it is difficult to set up a CA (Certificate Authority) and manage digital certificates at the scale required where there may be many millions of devices. Google has announced Certificate Authority Service. This is in beta and will provide a scalable and available service that simplifies and automates the management and deployment of private CAs.
My Opinion
These announcements from GCP underpin the view that organizations are increasingly using cloud services for their business-critical applications as part of their digital transformation journey. This is leading to more scrutiny of the ways in which these services can help the organization to support their own specific security and compliance obligations. The customer still needs to map these controls back to their obligations and to ensure that the controls are effective.
While none of the announcements from GCP are for offerings that are completely unique they do provide useful differentiation that may sway some customers to choose GCP. However, most organizations will have a hybrid IT deployment model involving multiple CSPs as well as on services delivered on-premises and this will remain a significant challenge for the foreseeable future.
For more details on this check out KuppingerCole research focusing on Hybrid Cloud Security, How to Protect Your Cloud Against Hacks and Industrial Espionage, Security Organization Governance and the Cloud, and Infrastructure as a Service – Global Providers.












































