15 to 20 years ago, a virus scanner – or let me call it Endpoint Protection – on your private or corporate computer was standard. Today, you must also have something like a virus scanner on your endpoint device. But in 2020, is it sufficient to detect viruses, worms, and rootkits or botnets like we did in the past? There have been a lot of changes in the way attackers try to steal data, get access to your computers, or even block you from working with your computer. This evolution must be part of your strategy for protecting your endpoints. It is called Endpoint Protection, Detection and Response (EDPR) – adding Detection and Response to your virus scanner.
Scanning suspicious files based on a signature is dead
I hope you agree that when it comes to endpoint protection, a classic virus scanner alone is no longer enough in the fight against the "bad guys". Anti-malware is necessary, but you need a lot more besides. And yes, security for endpoint devices plays a central role in your overall security strategy – you might also call it “Zero Trust” strategy. Endpoints today are way more than traditional PCs and notebooks. It is any device you interact with, including computers, virtual desktops, servers, smartphones, tablets, and IoT or SCADA devices. They all must be part of your strategy to prevent harm to your organization.
Investing into a single tool that can detect malware based only on patterns is very outdated because attackers are now focused on collecting data from your organization or blackmailing you via a ransomware attack. Attackers are continually trying to trick your employees into clicking on links to enter their credentials on a manipulated website or to download malware to get access to your organization. Your strategy must cover this, and EDPR meets this requirement.
Protection means to detect before, during, and after the execution
Protecting an endpoint is a broad field, and with Artificial Intelligence (AI) and Machine Learning, it is changing a lot. Real AI is much more efficient in detecting creatively implemented malware which might use exploits and change its signature frequently. Detection at runtime is essential, but difficult. Traditional tools focus more on pre-execution detection based on a static signature of a piece of malware.
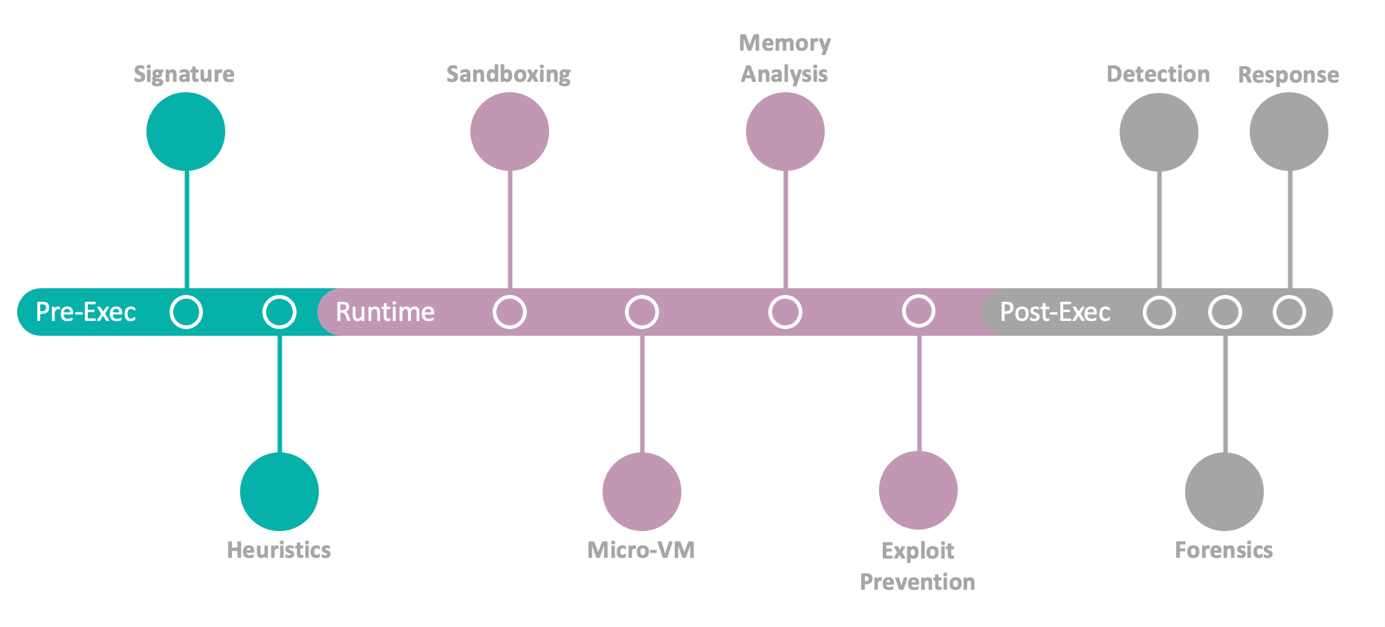
Looking more at the behavior of a malware and having tools which help to detect an attack, even after it happened, is also important. If attackers are currently in your system and preparing a bigger attack by infecting your servers with ransomware, for example, this needs to be detected. This is called post-execution and typically involves forensic analysis to enable organizations to respond to an attack even after it has begun.
The focus of such tools must be understood
Defining the broad range of use cases to protect an endpoint can be overwhelming at first. In light of this, it could be useful to consider the following:
- Protecting your endpoints with a combination of detection and prevention features. The local agent should be able to prevent an employee from executing a compromised file, as well as be able to detect malware post-execution, based on more complex detection mechanisms.
- Threat intelligence features should detect threats based on the behavior of the threat and knowledge from other attacks and be able to respond automatically to such an attack to prevent further harm to your organization.
- Advanced alerting and reporting mechanisms can help to identify the health state of endpoints on a central dashboard and be able to react to threats by collecting relevant information.
Do you use already use tools like this in your organization? Is the device you are currently using part of this protection strategy? If you are interested in this topic and feel that you still need some more input, you can join our next KCLive Tool's Choice session online on November the 9th, free of charge.











































