Addressing cybersecurity within a company often occurs in response to an incident which impacts a business’ operations. A cyber incident could be a data breach or malicious disclosure of internal information to the public. Ideally a company starts thinking about cybersecurity before they are forced to act by an incident. Preparations for a cyber incident can be made through an internal or external benchmarking of the cybersecurity landscape.
What to expect from a benchmarking exercise
To ensure a benchmarking preparation offers real value to the company, the expectations and outcome of the exercise should be clearly defined. An initial step should be to establish a standardized process for a company which allows it to repeat the process and to measure improvements. Benchmarking should provide an indication whether the current environment is ready for a future cyber incident or not. Being ready means having an open architecture which uses standards and is extensible. But it is not sufficient for a company to only look at technological aspects; the benchmarking exercise should provide a deeper insight into organizational topics. Every assessment should show if there are some organizational gaps and help to create a roadmap to fix them soon.
Benchmarking should focus on technology and organization
From our experience, discussions between KuppingerCole representatives and the many relevant stakeholders within an organization improve the quality of the resulting benchmarking tool. Stakeholders are architects, managers, developers, (internal) customers up to the C-Levels, because they all have different perspectives on cybersecurity and other requirements that need to be united. Bringing the varied stakeholders together means discussing various areas of the company. Usually we use our 12 categories for that - 6 organizational aspects and 6 technological aspects.
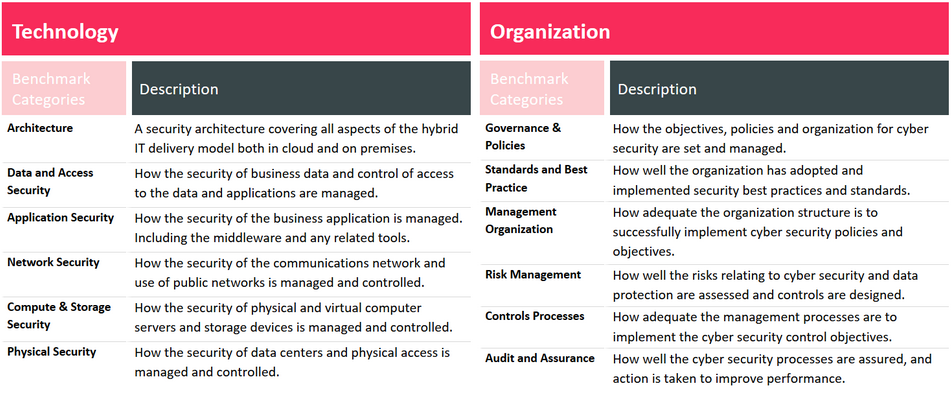
Focusing on these areas ensures that cybersecurity is seen from the beginning to the end and gaps within a single or multiple areas can be discovered.
Collect information, compare, and define concrete measures
After knowing the relevant areas that are decisive for benchmarking, the next step is to collect the information. There are various documents and guidelines to be evaluated, but also many interviews with teams and stakeholders must be carried out. The best result can be achieved with a set of good questions covering the various areas, with answers from different people, which can be rated by each category.
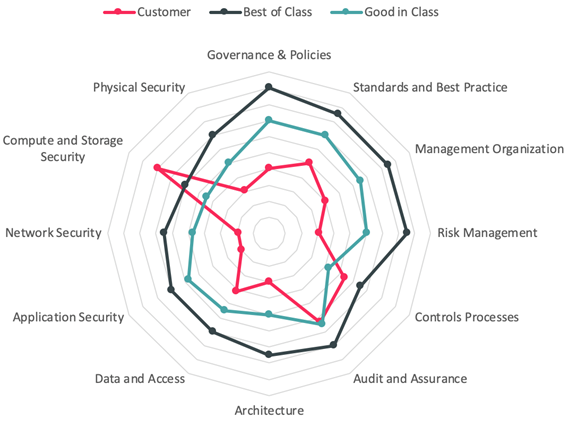
A graphical visualization with a spider graph allows an easy and fast overview of strengths and weaknesses. One goal of the benchmarking exercise is to create comparable results. This could be done with peers, between maturity levels, or with old benchmarking results. Quality comparative data is quite difficult to generate internally, and it is recommended to have external support.
Understand the result and define a roadmap
The spider graph and the documented benchmarking gives a good insight into the weaknesses of a company. In this example the company has weaknesses in Network Security, Application Security and Risk Management, so the next step should be to prioritize the open topics in those areas. This company should take a deeper look into what is missing and what needs to be improved while also focusing on future requirements. Doing this allows a company to create both a general and a detailed roadmap for planning the next steps to improve the cybersecurity within your company.
Benchmarking the cybersecurity landscape is a complex process and it is difficult to define a metric internally where you can compare yourself to. If you want to benefit from the experience and knowledge of KuppingerCole, our methodology, and our comparable data, feel free to ask for assistance. We can support you!










































