BYOD (Bring Your Own Device) is one of the hot topics of today’s IT. Many vendors promise to solve the BYOD challenges, with MDM (Mobile Device Management), MAM (Mobile Application Management), or other technologies. Most of these technologies fix some of the problems. But all of them fail in the great promise of solving all of your BYOD challenges.
Even worse, solving BYOD challenges is not what you should really care about. BYOD is just a symptom of a far bigger evolution. This evolution is about what my colleague Craig Burton just recently called “The Computing Troika” – the three major changes we are facing: Cloud Computing, Mobile Computing, Social Computing. This is about new delivery models for IT. It is about users using new types of devices (and more of them) inside and outside the corporate network. It is about opening up our communication for more external users, including our customers, leads, prospects, and so on. And it’s about communicating with them in a different way.
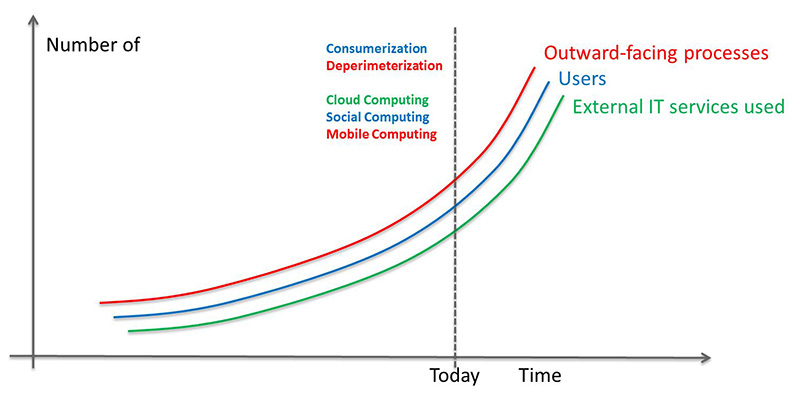
The situation we are facing today is that we are observing exponential growth in all these areas. We thus need to find other ways to deal with these evolutions.
BYOD in that context is just about supporting new devices for some specific groups of users. In the narrow context of BYOD most vendors have, it is about smartphones and tablets used by employees and maybe some groups of externalusers such as contract workers.
In a broader context, BYOD is about all types of devices which are not owned by the organization but are used to access corporate systems and corporate information. That might be the PC in the home office, the laptop of the auditor, the PC in the Internet Café, or whatever.
However, BYOD is just one part of that story. There is COPE and COD as well. COPE stands for Corporate Owned, Personally Enabled; COD is the acronym for Corporate Owned Device. In both areas, it is about supporting new types of devices like new smartphones, tablets and all the devices which will appear at the market within the next few years that we can’t even imagine today.
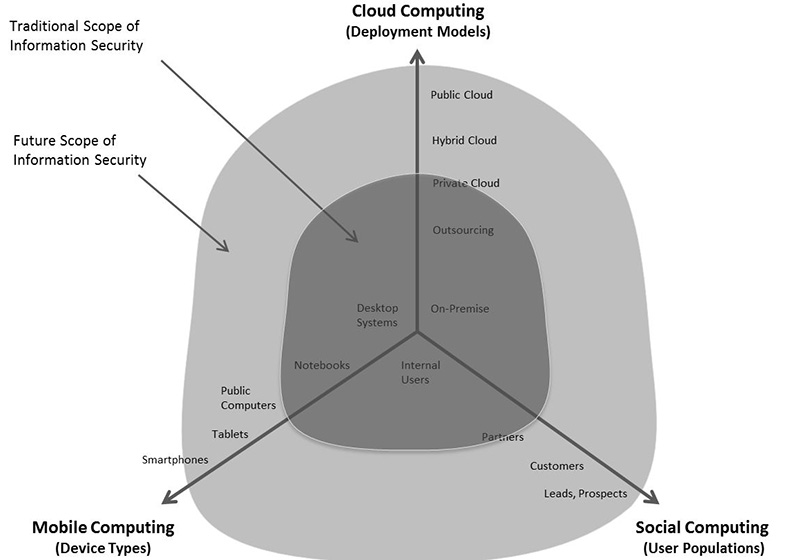
So from whatever perspective you look at BYOD, it is just a small subset of a bigger problem. The challenge is what the Computing Troika means for IT in general and Information Security specifically. This is about allowing all types of users using all types of devices access to corporate information and corporate systems, regardless of their deployment model.
If you solve that issue (which you have to do anyway) you have solved the BYOD issue. If you simply solve the BYOD challenge, you haven’t solved much. You probably have invested in some point solutions and some technology that fails in solving the challenges imposed by the Computing Troika. True, some of the approaches might provide value even in the bigger context. But that is something you don’t know for sure when just looking at the isolated BYOD issue, which most likely is not only or not even about BYOD – it might be COPE/COD and not BYOD at all, for instance.
So the simple message is: Don’t start investing in BYOD until you’ve understood the bigger context. Define your strategy for that. Understand what it means for Information Security and aspects like social logins, context-based authentication and authorization, your governance approaches, and so on. If you have got that big picture, you can start picking the technical pieces that help you. And furthermore, you can start solving all the legal, organizational, and governance issues around that.
There has been a KuppingerCole webinar on that topic – have a look at the podcast.











































